Over the past couple of weeks, security teams have been faced with a flood of reports of voice phishing (vishing) attacks. Malicious actors, including the ShinyHunters threat group, have used this technique to target Salesforce databases, with reports of very high profile victims, ranging from Google to Workday. More attacks are likely in the short term, both because copycat attacks are common and because attackers know defenders will eventually mitigate the attack. This puts security teams under pressure to respond quickly, but at the same time, they need to proceed cautiously, as business-critical applications such as Salesforce cannot be disrupted.
Understanding the Vishing Attack: A Focus on the Browser
This is where solutions such as Menlo Adaptive Web provide defenders with a powerful tool: a mechanism to enrich and alter the behavior of web applications inline. To understand why, let’s first outline key steps in a vishing attack. To gain access to an application, the attack targets a mechanism known as an OAuth device authorization grant.
The attacker, posing as IT staff during a phone call, tricks an authenticated user into entering a verification code on a page provided by the legitimate application. Many people have encountered a similar workflow in the context of authorizing smart TVs to access streaming accounts (such as Netflix) by entering a code on their phone, where they are logged in already, rather than needing to enter credentials on the TV. Salesforce, as well as other enterprise apps including Microsoft Entra ID and GitHub, offer such workflows. Crucially, unlike in many other phishing attacks, this code is entered in a legitimate web application. This means tools to block attacker infrastructure (URLs, IPs, reputation…) will not help here.
Why Traditional Methods Fall Short
At this point, security teams would ideally want to let users know they should be careful. One way to do this is by sending an email, but these are likely to sit unread in the user’s inbox. Another significant challenge is that most security teams lack visibility into which of their SaaS applications are vulnerable to this type of attack. Many enterprises use dozens, if not hundreds, of SaaS applications, and the existence of this OAuth mechanism wasn’t on many people’s radar until recently.
Ideally, we want in-context, at-the-time-of-the-attack signaling, and this is where adaptive web tools come in. These tools allow an administrator to load code into the browser as the user interacts with the page. This code can then display additional information, such as warnings or contextual help. It can also alter workflows by adding extra user prompts or pre-filling forms.
How Our Team Deployed a Custom Mitigation
Our own Menlo security team decided to use our product to protect ourselves from this threat. We chose to deploy a Menlo Adaptive Web module to our own users, first deciding how we wanted to warn the user and then on heuristics to determine when to do so. The guiding principle was to balance reducing risk with avoiding major disruption. We also wanted to move fast, so there was little time for anything too sophisticated.
In the end, we decided on an overlaid message that the user must click through to proceed. This means if the message is displayed in error, the disruption is minimal. To decide when to display the message, the module looks at the URL and the page content, triggering in the presence of keywords found on a sample of pages observed during OAuth device authorization grant flows. This approach casts a broad net, but it avoids the need to have a comprehensive list of all vulnerable SaaS applications.
Here is what this looks like for a user visiting the GitHub device activation page:
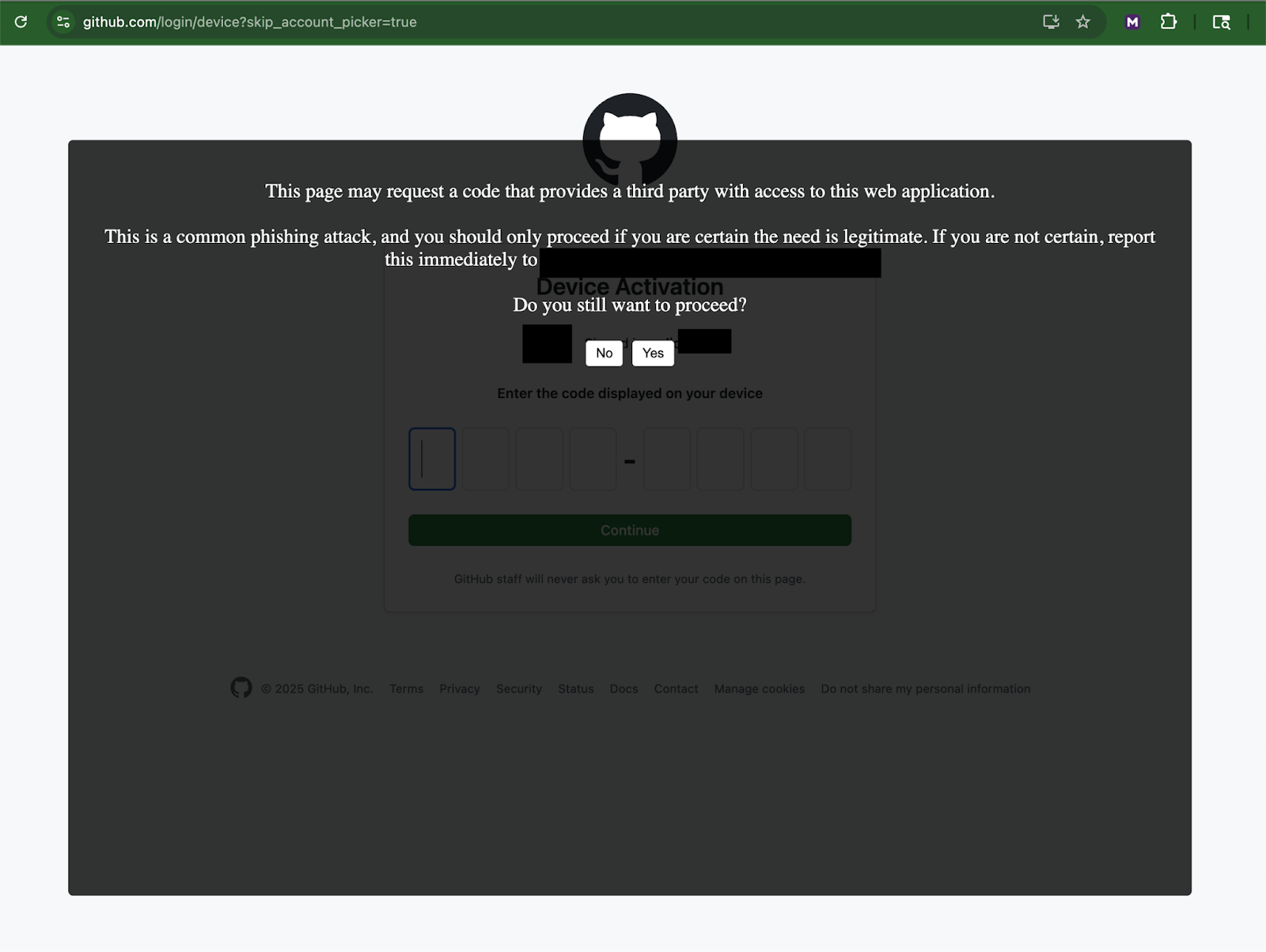
The team went from being asked to mitigate the risk to having this deployed to all our users, on all web browsers, in a matter of hours. The code for the module is simple, self-contained JavaScript, making it an ideal candidate for rapid development and even generative AI assistance. Menlo Adaptive Web modules are deployed to cloud browsers, meaning the team can also quickly iterate and refine the module.
To be clear, this is not a comprehensive solution to the problem, but it is a powerful mechanism that allows security teams to have a rapid, in-band response to novel and emerging threats across all their SaaS applications. It gives teams time to identify how to harden Salesforce and other SaaS apps against such attacks, figure out which stakeholders need to be involved in the changes, and plan how to safely implement them. This type of in-band security signaling is far more effective than broadcasting about the threat via email because it presents the warning at the exact moment the user is at risk.
Want to see Menlo in action? Schedule a demo with our team today here.



