A major cybersecurity investigation has uncovered a sophisticated criminal operation called Vault Viper that exploits online gambling platforms to distribute a malicious custom browser with remote access capabilities.
The threat actor, linked to the Baoying Group and connected to the Suncity Group—a major Asian crime syndicate—has created an unprecedented infrastructure combining iGaming software distribution with advanced malware deployment.
Security researchers from Infoblox Threat Intel, working with the United Nations Office on Drugs and Crime Regional Office for Southeast Asia and Pacific, discovered that the operation has potentially infected millions of devices worldwide.paste.txt
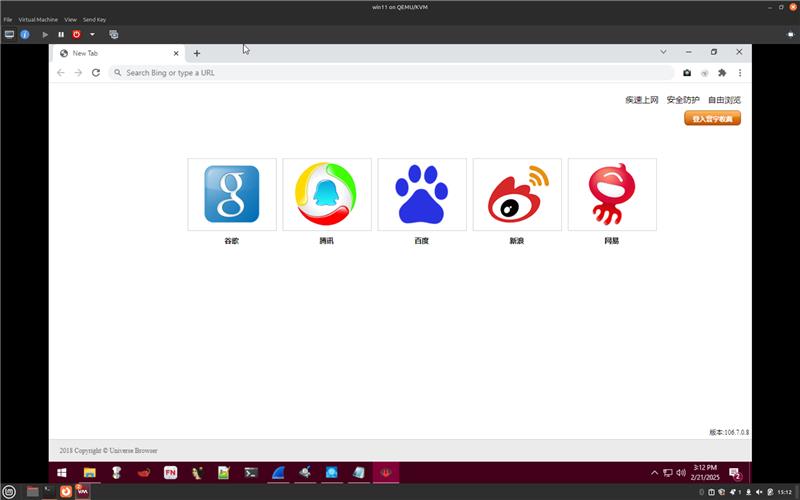
The Universe Browser, marketed deceptively as a privacy-friendly tool for bypassing censorship restrictions in countries where online gambling is prohibited, serves as the primary distribution vector for Vault Viper’s malicious payload.
However, analysis reveals that the browser contains multiple hidden programs operating silently in the background, including keylogging functionality, unauthorized network connections, and covert device configuration changes consistent with remote access trojans and other sophisticated malware.
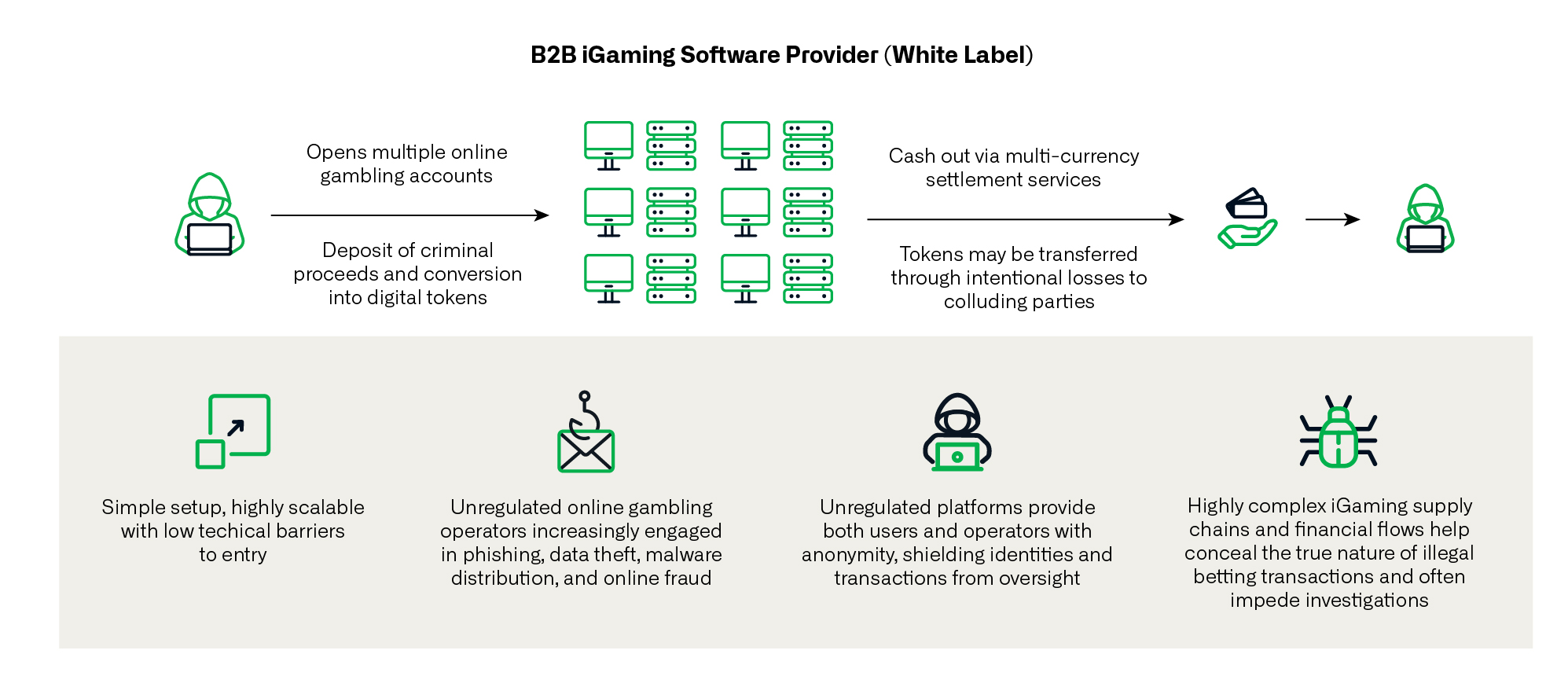

In recent years, these networks have aggressively diversified their business lines by pivoting from online gambling into cybercrime and online fraud, exploiting gaps in regulations of complex supply chains, transactions, and revenue streams involved in online gambling.
The deceptive marketing masks the browser’s true purpose: enabling persistent surveillance, credential theft, and large-scale monetization for criminal actors.paste.txt
Connection to Transnational Organized Crime
The investigation traces Vault Viper’s operations back to the Baoying Group, which operates through BBIN, one of Asia’s leading iGaming software suppliers, or “white labels.”
Despite these various configurations and tactics, we discovered a distinct DNS fingerprint for Vault Viper, making it possible to trace, map out, and attribute the activity.

This entity not only services illegal online gambling platforms but also distributes the malicious Universe Browser to unsuspecting users.
The research reveals deep connections to convicted Triad boss Alvin Chau and the Suncity Group, demonstrating how Vault Viper functions as a critical enabler of transnational organized crime in Southeast Asia.paste.txt
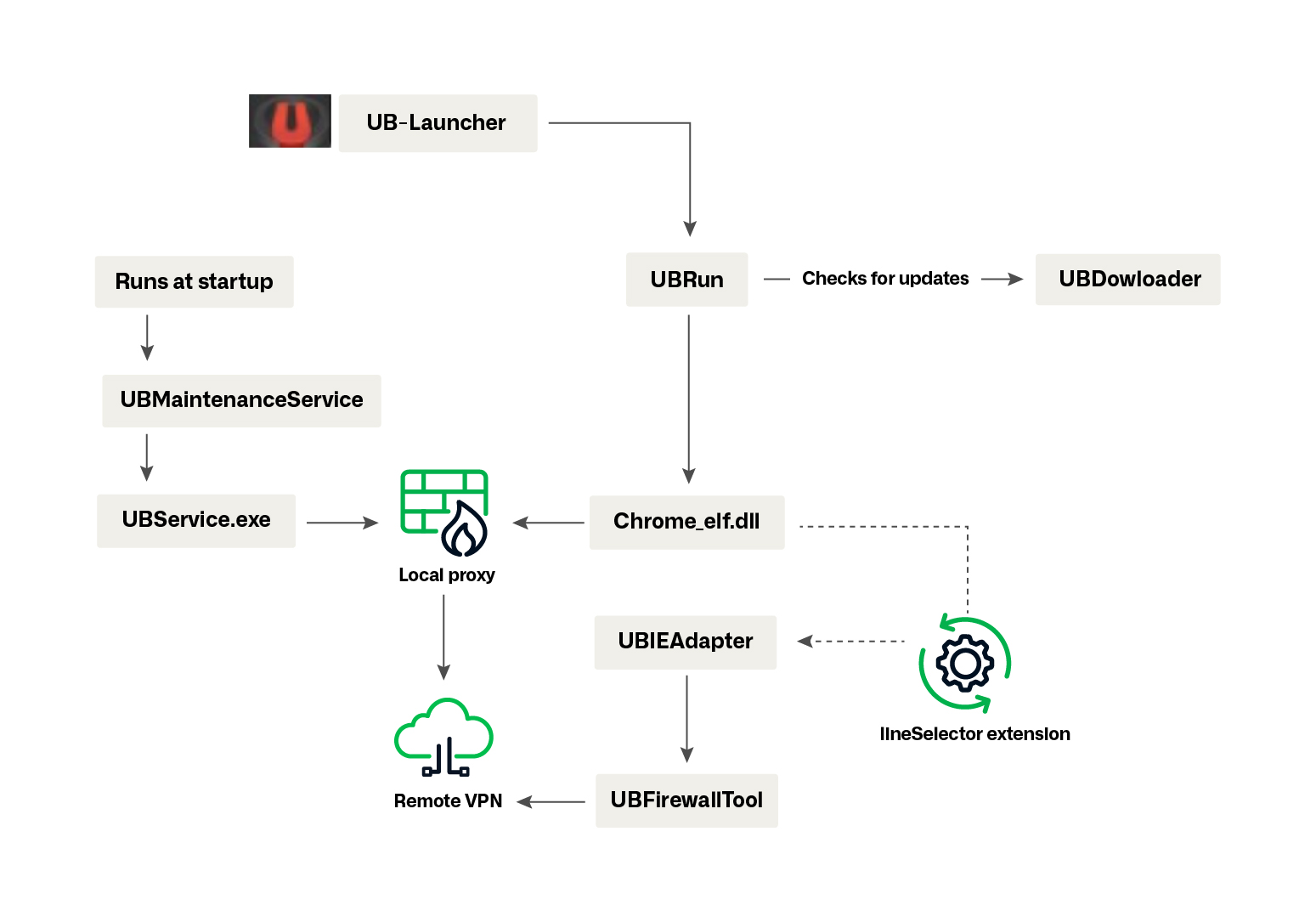
The operation represents far more than a simple malware distribution campaign. Researchers found that the custom browser, DNS infrastructure, and integrated services function as a comprehensive exploitation framework designed for sustained access and monitoring.
This includes “Screenshot” and “lineSelector,” both of which are specific to Vault Viper and not offered on the official Chrome Store.

The infrastructure encompasses tens of thousands of associated domains, with many still actively used by documented criminal networks, creating a vast and intricate web of command-and-control systems concealed through companies registered across dozens of countries.paste.txt
Southeast Asian Crime Syndicates
This discovery highlights an alarming trend in Southeast Asia’s cyber threat landscape, where criminal organizations have shifted from primarily online gambling operations into sophisticated cybercriminal enterprises.
These networks generate conservatively tens of billions of dollars annually through a combination of industrial-scale scam centers, cyber-enabled fraud operations, and money laundering schemes.
UBService is another QT5 app containing several embedded resources, in particular a large SQLITE3 table containing encrypted records.

The increased technical expertise and operational resilience of these groups have transformed them into some of the most underestimated threats facing the international community.paste.txt
Online gambling platforms have become the primary front for these criminal operations, serving as ideal vectors for concealing diversified cybercriminal activities, money laundering, and human trafficking networks.
The Vault Viper case demonstrates how unregulated iGaming suppliers have been exploited as distribution channels for advanced malware, with the Universe Browser serving as the perfect tool to identify wealthy players and gain unauthorized machine access.paste.txt
Researchers emphasize that this investigation represents unprecedented scope, with BBIN’s distribution of riskware marking a significant escalation in criminal sophistication.
The case underscores the urgent need for heightened awareness, regulatory frameworks, and international collaboration to address the complex and evolving threats emerging from Southeast Asia’s criminal networks.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.



