The cybersecurity community is once again watching APT37, a North Korean-linked threat group, as it launches spear-phishing attacks that lure unsuspecting users into downloading malicious files.
Recent tactics include:
- Archives (ZIP) containing oversized Windows shortcut (.LNK) files that hide Shellcode, PowerShell, and script files. These Powershell commands are used to decrypt and execute further payloads.
- Microsoft CHM files are used as droppers to deliver RoKRAT, enabling remote access and data exfiltration.
- Steganography, concealing malware inside innocent JPEG files to bypass antivirus, heuristics, and many EDR tools.
https://cybersecuritynews.com/apt37-hackers-weaponizes-jpeg-files/
According to Cyber Security News, the CHM and LNK files act as droppers — a common trick used by sophisticated threat actors to bypass conventional detection and gain a foothold in target networks before downloading the malicious payload for further compromise and control.
The Detection Problem
Detection and response is an important layer of any proper cyber defense architecture. But when prevention is lacking, it causes overwhelming alerts and fatigue on the backend, leading to unrealistic expectations on the SOC even when powered by AI-driven tools.
What’s needed is a balanced, prevention-first approach: one that can stop the threat before the user even sees it.
That’s where the integrated approach of browser isolation and data security comes in — delivering real-time protection without relying on threat detection or user judgment or bias in AI.
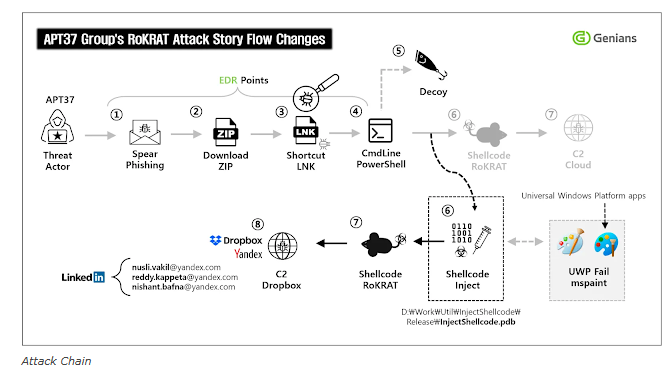
The Attack Chain: Initial Compromise with a Spear-Phishing Email with a Dropper Attachment
APT37’s recent campaign illustrates a classic cyber kill chain:
- Spear-phishing email delivers an archive (zip) which contains an oversized LNK or CHM to update the user’s machine.
- The victim opens the file, launching scripts or payloads hidden in the LNK or CHM files.
- RoKRAT malware is downloaded via Cloud API from Box, giving attackers further access and control.
But here’s what happens with browser & data security in place.
Breaking the Cyber Kill Chain
Step 1: The Malicious Email Attachment — Disarmed by CDR
If a user receives an archive with multiple LNK or CHM files (or any other document) as an attachment:
- CDR intercepts the email attachment in real time via seamless backend integration with no impact to user experience.
- The email attachment is disarmed of any malicious scripts and shellcode in just milliseconds via a method of duplication and copy, allowing only legit and known-good contents.
- A safe, usable file is delivered with all the functionality in the same original file format, leaving behind any of the malicious / unknown risks.
Result: The duplicated file is rendered harmless — even if it was previously weaponized.
Step 2: Weaponized Image or HTML via Dropbox — Isolated Through The Browser
APT37 also hides payloads in image files or HTML content hosted on Dropbox or similar platforms.
- With Browser Isolation: The content is opened in a cloud-based isolation container. The user sees and interacts with a safe rendering — but no code ever executes on their machine.
- Even when the user chooses to download the malicious image file, the image file is passed to CDR for duplication and copy, breaking the steganography technique and allowing the same quality image without any hidden components or suspicious shell commands.
Result: The exploit can’t run. The endpoint remains untouched.
Proactive Protection, Not Reactive Detection
This approach delivers true zero-trust file and web access:
- No need to constantly update and keep track of new detections of unknown threats — they simply never get to execute.
- Users stay productive, accessing files and web content as usual in the native original file format.
- Security teams get peace of mind knowing every download, every click, and every file is sanitized or isolated.
- SOC and EDR deployment are more effective and efficient without having to deal with false positives and noise.
Why It Matters
As threat actors like APT37 continue to innovate — hiding malware in images, documents, and web content — traditional detection-based tools fall short. You can’t rely on getting updated signatures or wait for alerts after compromises to respond and contain a breach.
With a browser isolation and data security solution, you stop attacks at the source:
- Spear-phishing attachments neutralized
- Weaponized drive-by downloads contained
- Hidden malware in images or archives disarmed
This isn’t just another security layer. It’s a new way to eliminate risk — before it reaches your environment.
Ready to Stop APT37?
APT37 and other nation-state groups are raising the stakes. You can’t afford to wait for alerts after a compromise.
See how Menlo Security delivers zero trust web and file security that stops threats like APT37 before the first click:



