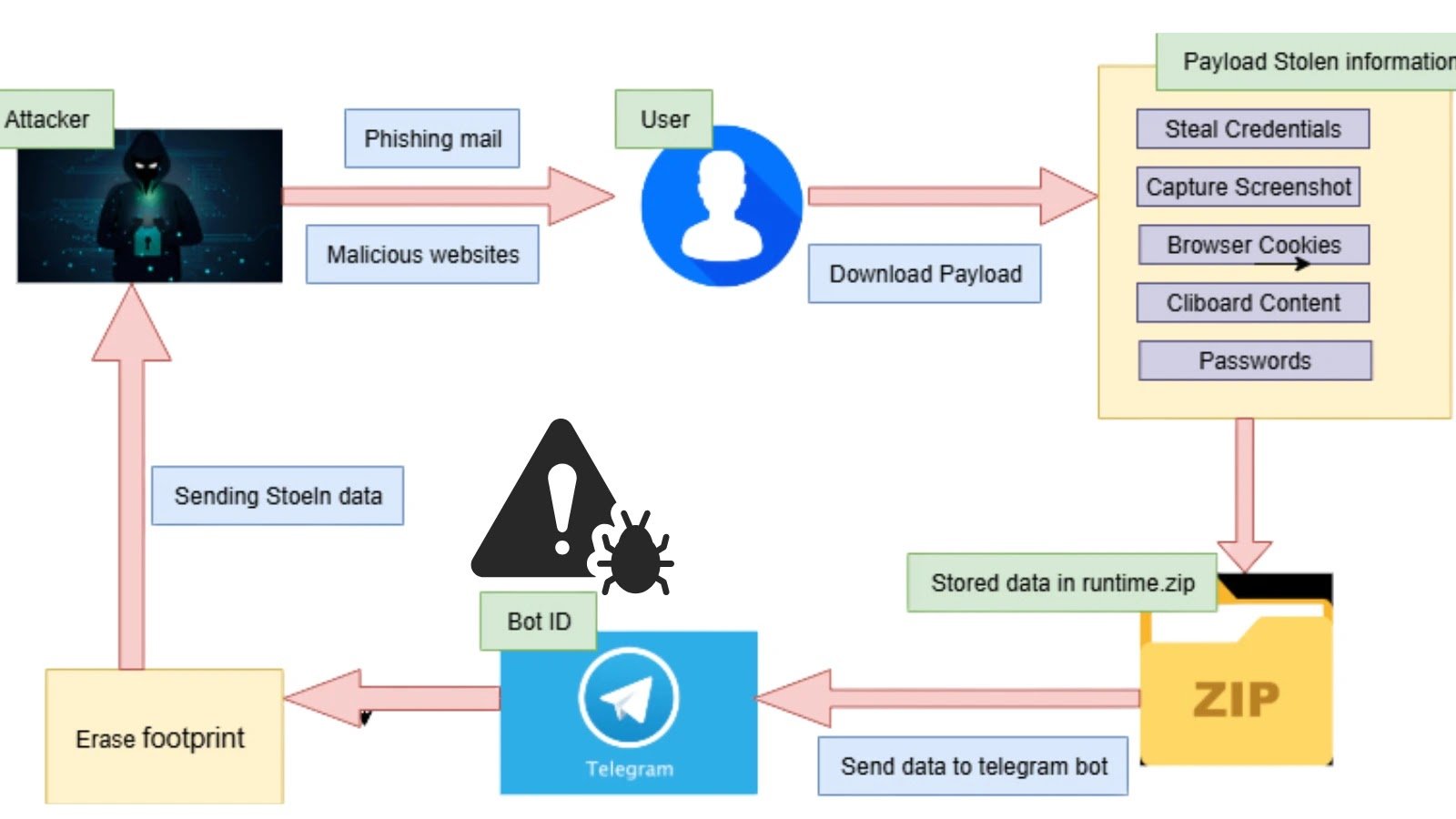
Shuyal Stealer is a recently uncovered infostealer that pushes the boundaries of traditional browser-targeted malware.
Unlike most variants that zero in on popular platforms like Chrome and Edge, Shuyal dramatically widens its scope by targeting 19 different browsers, making it far more versatile and dangerous in its data-harvesting capabilities.
Beyond the usual theft of browser-stored credentials, Shuyal conducts deep system reconnaissance, harvesting granular details about disk drives, input peripherals, and display configurations.
It also captures screenshots and clipboard contents, adds Discord tokens to its haul, and channels everything out through a Telegram bot infrastructure, rendering it a highly efficient and stealthy exfiltration tool.


Shuyal Stealer is delivered as a 64-bit C++ executable compiled into an obfuscated binary. Its integrity hashes are MD5: 9523086ab1c3ab505f3dfd170672af1e and SHA-256: 8bbeafcc91a43936ae8a91de31795842cd93d2d8be3f72ce5c6ed27a08cdc092.
A unique identifier in its PDB path gave rise to the “Shuyal” moniker. Upon execution, the malware leverages Windows Management Instrumentation (WMI) commands such as
textwmic diskdrive get model, serialnumber
wmic path Win32_Keyboard get Description, DeviceID
to extract detailed hardware fingerprints. This reconnaissance not only maps disk drive specifications and input device identifiers but also inventories display setups, enabling Shuyal to tailor its tactics to each victim’s environment.

Credential harvesting begins with a targeted SQL query against browser-stored SQLite databases:
textSELECT origin_url, username_value, password_value FROM logins
This command retrieves saved credentials from a wide array of browsers—Chrome, Edge, Tor, Brave, Opera, Opera GX, Yandex, Vivaldi, Chromium, Waterfox, Epic, Comodo, Slimjet, Coc Coc, Maxthon, 360 Browser, Falkon, and two lesser-known variants.
By casting this wide net, Shuyal maximizes its potential for account compromise across different platforms and regions.
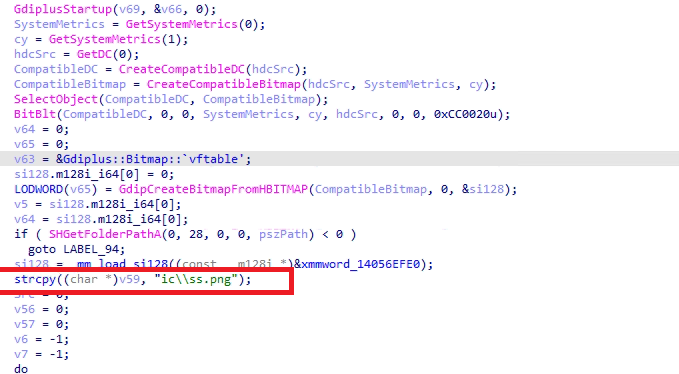

It also captures clipboard text via the OpenClipboard and GetClipboardData APIs, saves screenshots using GdiplusStartup, BitBlt, and GdipSaveImageToFile, and extracts Discord tokens from all standard client installations.
Infection, Evasion, and Persistence
Shuyal’s infection chain begins with a malicious executable that creates a “runtime” directory to stage collected data.
A PowerShell script then compresses this directory into a ‘runtime.zip’ archive, which is exfiltrated over Telegram’s Bot API using a hardcoded bot token and chat ID.
Once exfiltration completes, the malware uses a batch file “util.bat” to self-delete traces, including both the compressed archive and residual browser database files, minimizing forensic footprints.
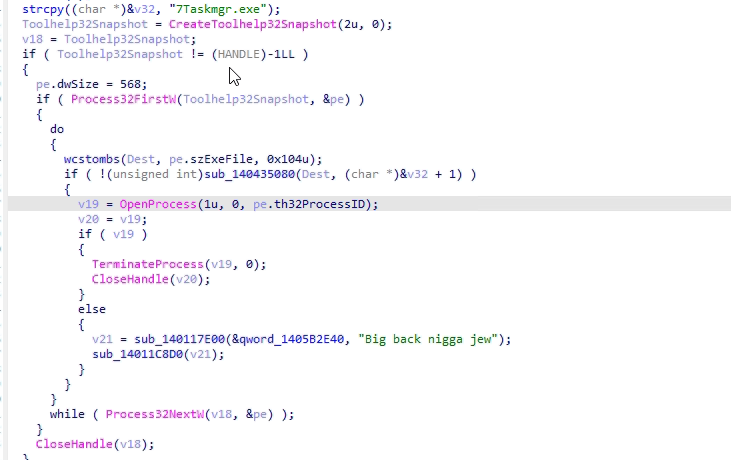
Evasion techniques are particularly unsettling. Immediately after launch, Shuyal scans for taskmgr.exe, forcefully terminates it via the TerminateProcess method, and sets the DisableTaskMgr registry value to 1 to prevent manual process inspection.

Persistence is achieved when Shuyal silently replicates itself into the Windows Startup folder using the CopyFileA API, ensuring execution on every reboot.
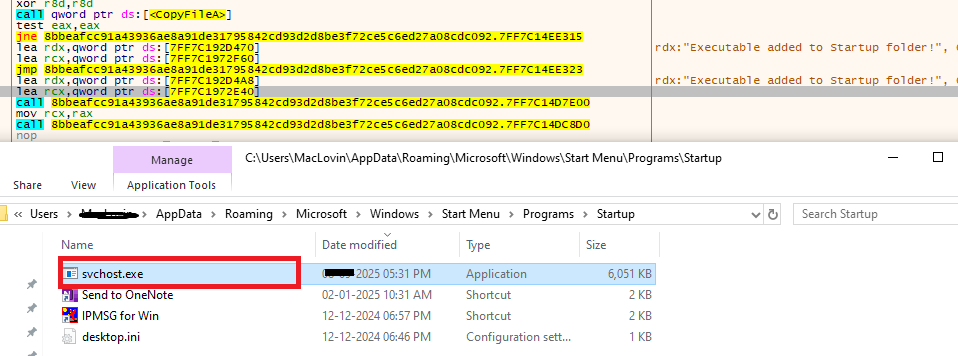

Vigilance, regular software patching, and behavior-based security controls are essential to defend against this formidable infostealer.
Mitigations
Removing Shuyal Stealer requires safe-mode intervention and specialized tooling. Victims should reboot into Safe Mode with Networking to hinder active processes, then deploy a reputable antivirus such as UltraAV, which identifies the threat as Trojan.W64.100925.Shuyal.YR.
Manual removal involves deleting malicious files from the Startup folder and cleaning registry values that disable Task Manager. Administrators can further detect and block PowerShell-based exfiltration by auditing command-line logs and restricting script execution policies.
Shuyal Stealer’s combination of broad browser targeting, deep system profiling, aggressive evasion, and stealthy exfiltration underscores its danger to user privacy and organizational security.
By intercepting login credentials, system configuration data, clipboard contents, and authentication tokens, Shuyal enables attackers to conduct precise identity theft, unauthorized account access, and targeted follow-on attacks.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.