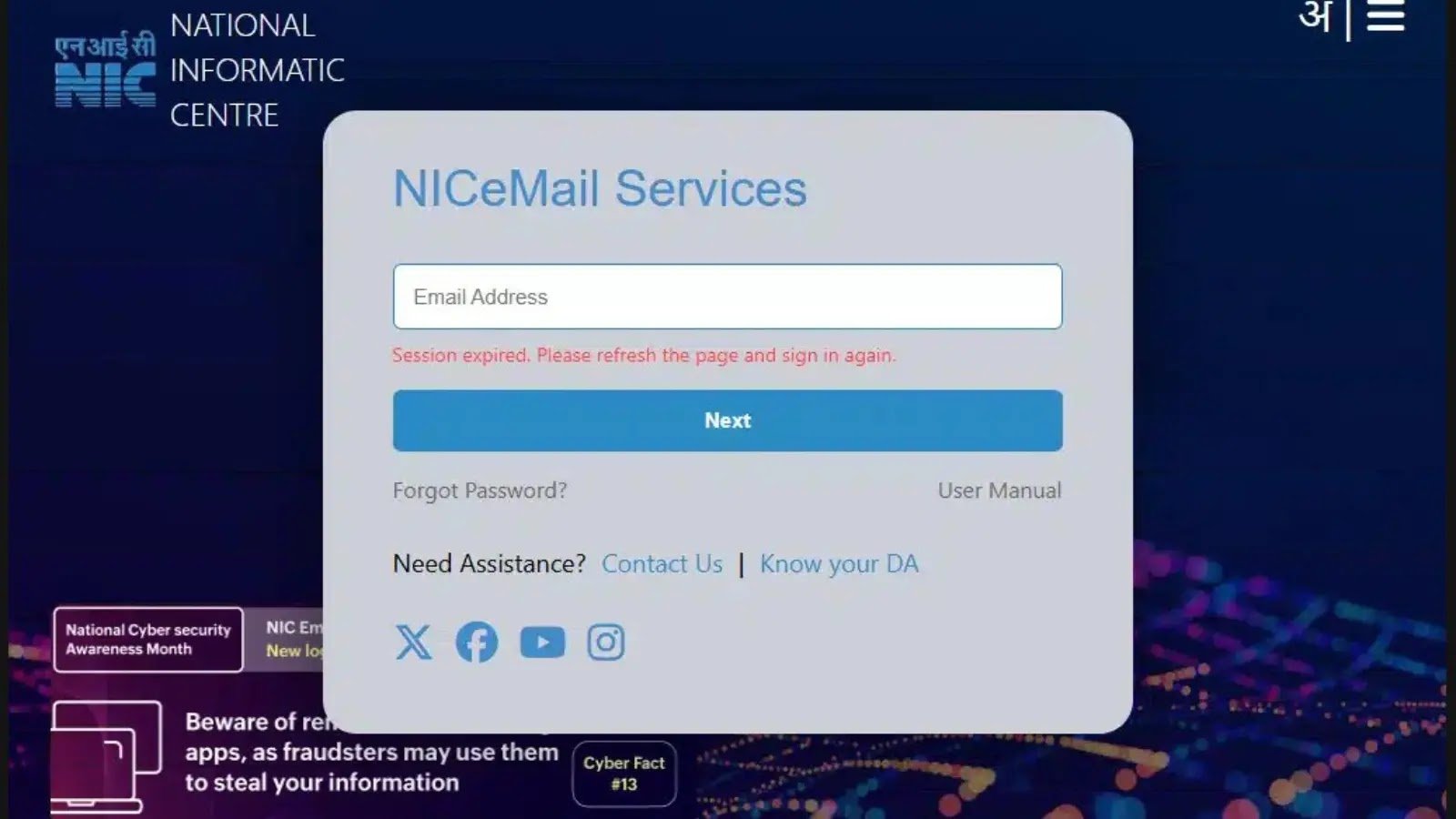
Pakistan-based advanced persistent threat group APT36, also known as TransparentTribe, is actively targeting Indian government entities with a sophisticated spear-phishing campaign using email lures themed as “NIC eEmail Services.”
This campaign leverages lookalike domains and weaponized infrastructure to steal credentials and enable long-term espionage.
The attack begins with email messages that convincingly mimic official notifications from the National Informatics Centre (NIC), the Indian government’s digital backbone for email and IT services.
Victims are presented with a fake login portal branded as “NICeMail Services,” designed to harvest sensitive information such as email addresses and passwords.
The login page closely imitates the legitimate NIC webmail interface, further enhancing the campaign’s authenticity and likelihood of success.


The malicious infrastructure supporting this operation comprises several domains and servers linked to recent APT36 activity:
- accounts.mgovcloud[.]in.departmentofdefence[.]live: This domain hosts the phishing page, spoofing the look and feel of NIC’s authentic web portal, and harvests user credentials submitted on the fake login form.
- departmentofdefence[.]live: Acts as a parent domain, lending additional credibility through its suggestive government affiliation.
- 81.180.93[.]5: Linked to a “Stealth Server” Command & Control (C2) interface, accessible over port 8080. This panel is used to receive data exfiltrated from infected systems and to control malware implants deployed post-compromise.
- 45.141.59[.]168: Another IP involved in the campaign, potentially hosting malware payloads or facilitating C2 communications.
Network scanning data confirms a valid TLS certificate for the phishing domain, indicating an extra layer of operational security to avoid browser warnings and reinforce legitimacy in the eyes of targeted users.
TransparentTribe’s Persistent Espionage
APT36, or TransparentTribe, is a notorious threat group attributed to Pakistan with long-standing interests in Indian defense, diplomatic, and government organizations.
The group’s modus operandi typically involves spear-phishing and tailored malware delivery to facilitate data theft and espionage.
APT36 employs continually evolving tactics, including highly realistic phishing pages, usage of open-source attack frameworks, and exploitation of current geopolitical events to enhance the likelihood of victim engagement.
This latest campaign, masquerading as a routine NIC service notification, exemplifies the threat group’s ability to exploit trust and evade basic security controls.
Mitigations
Security experts advise Indian government users and affiliated organizations to exercise heightened vigilance, particularly when prompted to enter credentials on any unexpected or unofficial login portals.
Indicators of compromise such as the domains and IP addresses listed above should be blocked at the network level, and users should be educated about the telltale signs of spear-phishing.
IT departments are urged to roll out multifactor authentication and continuously monitor for credential abuse or anomalous logins, as these measures can help thwart APT36’s primary attack vectors.
Given the group’s persistence and adaptive strategies, proactive defense and cyber hygiene remain critical to safeguarding sensitive government systems against state-sponsored threats.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.