Microsoft’s name and branding have long been associated with trust in computing, security, and innovation. Yet a newly uncovered campaign by the Cofense Phishing Defense Center demonstrates that even the most recognized logos can be hijacked by threat actors to exploit user trust.
By blending classic social engineering tactics with advanced deceptive overlays, this scam not only harvests login credentials but also induces victims to call fraudulent support lines—handing attackers direct remote access.
The attack begins with an innocuous-looking email, purporting to be a payment notification from a fictitious “Syria Rent a Car.”
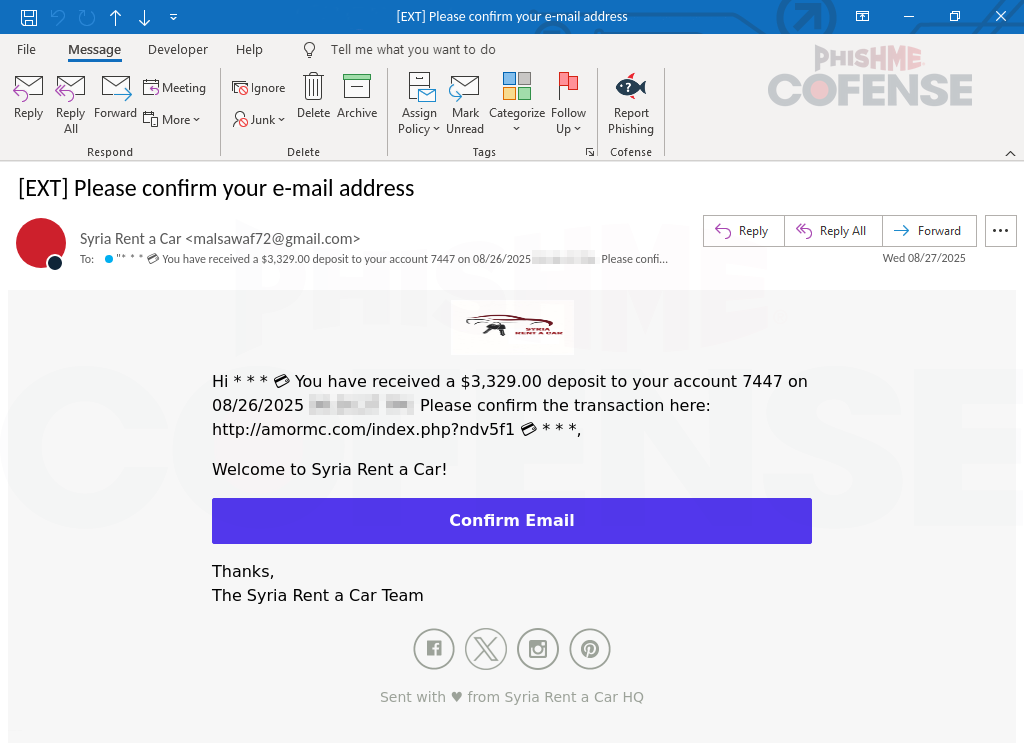

In reality, the “payment lure” is a ruse to pique recipients’ curiosity and prompt them to click the embedded link. Once clicked, users encounter a counterfeit CAPTCHA challenge designed to appear legitimate.
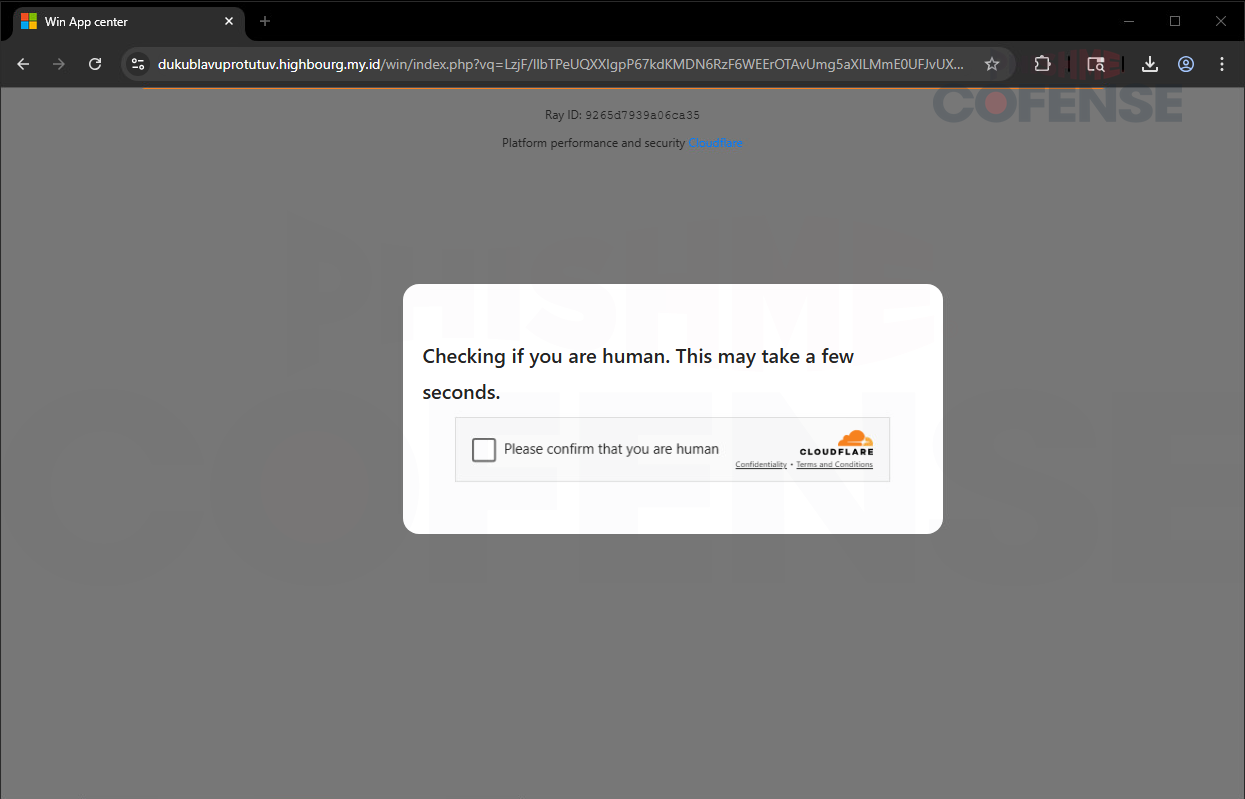

This step serves a dual purpose: it convinces victims they are interacting with a trusted service while also deterring automated scanners from flagging the page. After “passing” the CAPTCHA, unsuspecting users are redirected yet again—to the core of the scam.
Faux Ransomware Experience
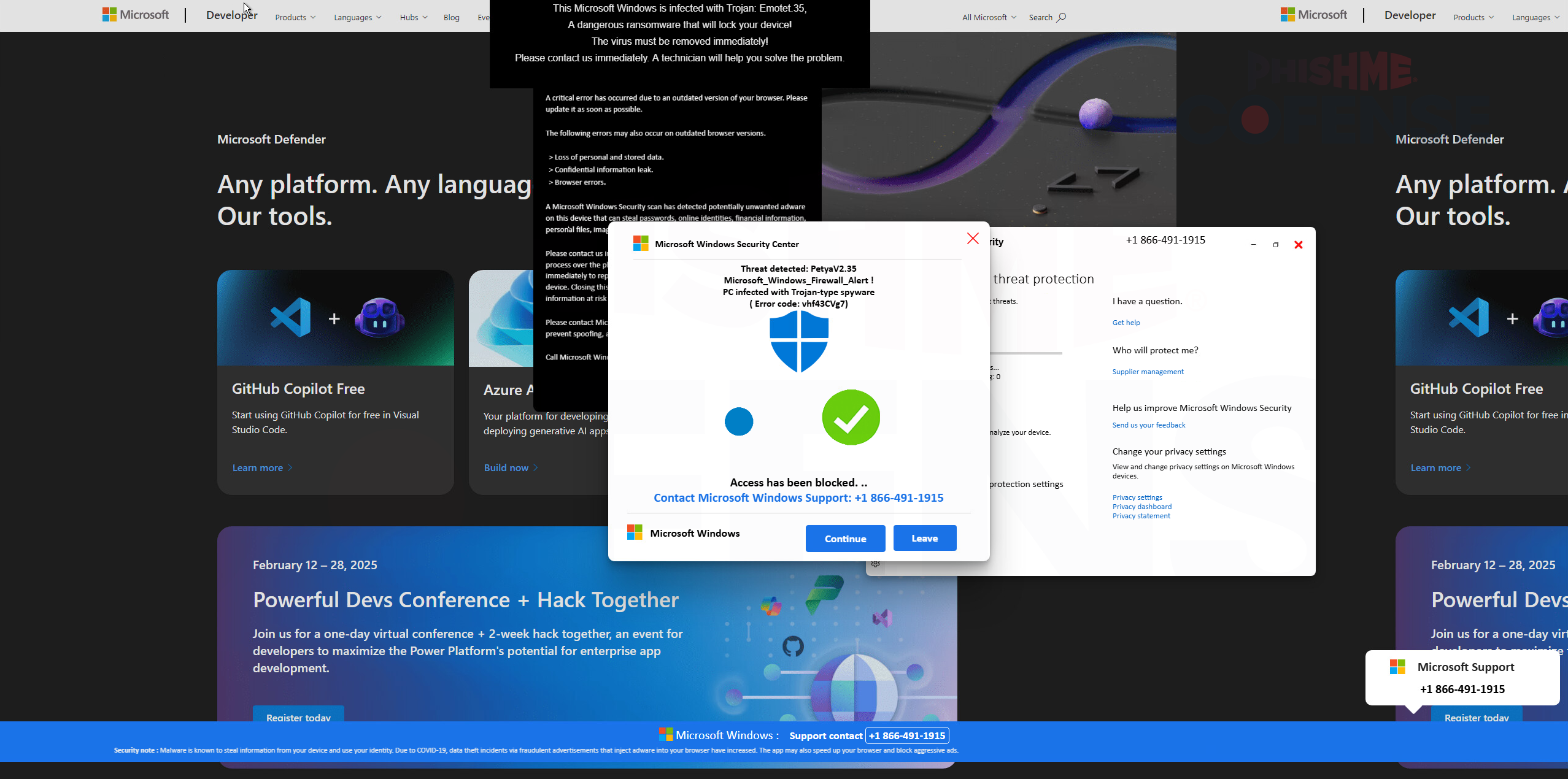
Unlike typical phishing schemes that quietly capture credentials, this campaign escalates the deception by simulating a browser lockdown.
Victims find their cursor immobilized, multiple pop-ups resembling Microsoft security alerts flooding the screen, and an urgent message claiming that the system has been compromised.
This forced loss of control mimics ransomware behavior, creating panic and urgency. Unbeknownst to the victim, a simple press of the ESC key can restore control, but the alarming visuals and repeated Microsoft logos drive users to believe their only recourse is to contact “Microsoft Support” via the prominently displayed phone number.
When victims call the fraudulent support number, they are connected to actors posing as Microsoft technicians.
At this stage, attackers employ high-pressure tactics—requesting account credentials or persuading users to install remote desktop software.
With remote access tools installed, threat actors can infiltrate networks, exfiltrate data, deploy malware, or pivot to more critical systems.
.png)
.png)
The combination of on-screen panic and authoritative logos makes the scam particularly effective against users who assume a call labeled as “Microsoft Support” must be genuine.
Technical Indicators and Observed URLs
Cofense’s analysis identified several infection and payload URLs. Initial links include hxxps://alphadogprinting[.]com/index.php?8jl9lz and variants hosted on amormc[.]com resolved to IPs such as 107[.]180[.]26[.]155 and 184[.]168[.]97[.]153.
Subsequent payload stages delivered landing pages from domains like toruftuiov[.]com and highbourg[.]my[.]id, all mapping to various Cloudflare IPs (104[.]21.32.1, 104[.]21.112.1, and others) and endpoints such as 18[.]160.41.101. These technical indicators can assist defenders in blocking malicious traffic and identifying compromised clients within enterprise networks.
This campaign underscores the need for layered defenses and continual security awareness training.
First, organizations should implement email filtering that inspects links for known phishing domains and anomalies in sender information.
Second, user education must emphasize skepticism toward unsolicited payment notifications, even when presented under a reputable brand.
Third, endpoint security solutions capable of detecting unusual browser behaviors—such as simulated lock screens—can raise alerts before users escalate to calling fraudulent support.
Finally, maintaining up-to-date incident response playbooks, including procedures for verifying legitimate support channels, can prevent victims from inadvertently handing over credentials or remote access.
The weaponization of Microsoft’s logo in this scam highlights a sobering reality: brand recognition can be exploited to bypass users’ defenses.
By combining payment lures, fake CAPTCHAs, deceptive UI overlays, and phone-based social engineering, attackers create a multilayered trap that preys on trust and urgency. Vigilance remains the most effective defense.
Security teams and end users alike must question unexpected prompts, verify support contacts through official channels, and rely on a comprehensive security posture to stay one step ahead of sophisticated phishing campaigns.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.