Threat researchers at Netskope have uncovered a sophisticated new Remote Access Trojan (RAT) written in Python that masquerades as “Nursultan Client,” a legitimate Minecraft application popular in Eastern-European and Russian gaming communities.
The malware leverages the Telegram Bot API as its command-and-control (C2) channel, enabling attackers to exfiltrate stolen data and maintain persistent access to compromised machines.
This discovery underscores a troubling trend of cybercriminals targeting the gaming community through malicious mods, cheats, and counterfeit tools.
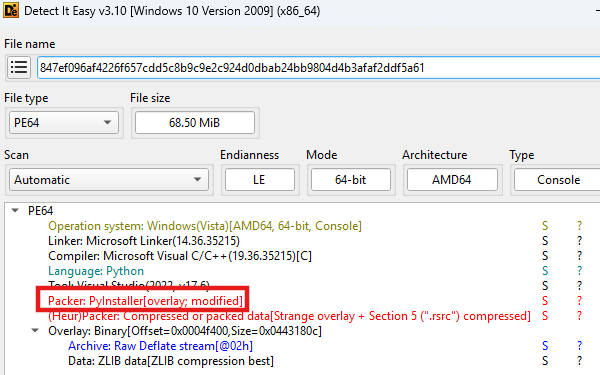
The Python RAT was initially discovered during threat hunting activities as a 68.5 MB executable compiled with PyInstaller.
While the tool is commonly used for legitimate purposes, malware authors frequently exploit it to package malicious Python scripts with their dependencies into standalone files.

Upon execution, the malware immediately employs deception tactics, displaying a fake installation progress bar bearing the “Nursultan Client” name to trick unsuspecting users into believing they are installing legitimate software.
Although certain persistence and credential-stealing mechanisms are Windows-specific, the malware’s core C2 communications and surveillance features operate across Windows, Linux, and macOS systems, dramatically expanding its potential victim base.
The attacker’s use of the Nursultan Client name in both fake installation messages and persistence registry keys demonstrates a deliberate social engineering strategy specifically designed to deceive the gaming community.
Telegram as an Invisible C2 Highway
The malware’s operational backbone relies entirely on Telegram’s Bot API for command execution and data exfiltration.
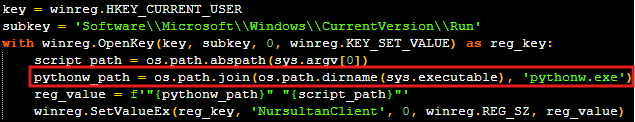
The persistence code is designed for a raw Python script and incorrectly constructs the startup command for the compiled executable.

Security researchers discovered hardcoded Telegram credentials—including a bot token and authorized user IDs—embedded within the executable.
This approach allows threat actors to hide their malicious communications within a privacy-focused messaging service, making detection significantly more challenging for security teams.
Only authorized attackers can issue commands to infected machines, creating a controlled environment for launching targeted operations.
The malware arsenal includes numerous dangerous capabilities accessible through simple text commands. A “/tokens” command specifically targets Discord authentication tokens by scanning Discord client local storage files and searching through major web browsers including Chrome, Edge, Firefox, Opera, and Brave.
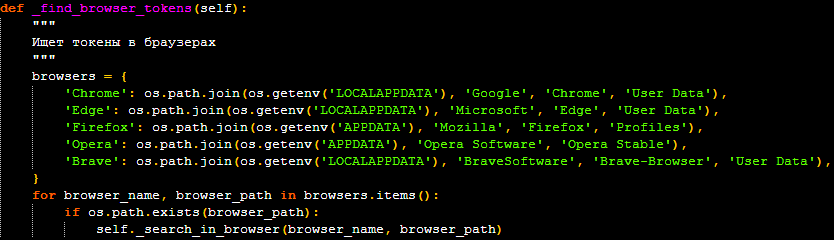

Stolen Discord tokens can be weaponized to hijack user accounts and compromise gaming communities.
The “/info” command performs detailed system reconnaissance, collecting computer names, usernames, operating system versions, processor information, memory and disk usage data, and both local and external IP addresses.
System profiles are formatted in Russian and include the malware author’s signature “by fifetka.”
Beyond credential theft, the RAT offers surveillance functionality through “/screenshot” and “/camera” commands, enabling attackers to capture desktop screenshots and webcam photographs transmitted directly through the Telegram channel.
Adware capabilities allow attackers to open arbitrary URLs in victims’ browsers or display pop-up messages and images, potentially facilitating phishing attacks or malicious advertisements.
Indicators of Lower-Tier Threat Operations
The absence of advanced anti-analysis techniques, custom code obfuscation, and the hardcoded “ALLOWED_USERS” licensing structure suggest a Malware-as-a-Service operation designed for lower-level threat actors rather than an advanced persistent threat group.
Despite its feature-rich capabilities, analysis reveals the malware author lacks sophisticated tradecraft. Flawed persistence mechanisms would likely fail due to incorrect Python path construction and reliance on temporary PyInstaller directories.
Organizations should implement deep visibility into encrypted traffic, monitor for suspicious Telegram API communications, and educate users about verifying software authenticity before installation to mitigate risks from this emerging threat.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.



