Luma Infostealer, a malware-as-a-service (MaaS) offering, has emerged as a potent threat targeting high-value credentials such as web browser cookies, cryptocurrency wallets, and VPN/RDP account information.
Beyond isolated theft, threat actors are employing Luma in the initial infiltration stages of complex campaigns—ransomware deployment, account hijacking, and internal network compromise.
The stolen data fuels identity theft, financial fraud, and corporate intrusions. Strengthening endpoint detection and response (EDR) systems—with behavior-based detection and threat intelligence integration—is critical for effective defense.
In recent years, infostealer malware has evolved into a primary high-risk vector for both individuals and organizations.
These threats operate surreptitiously on victims’ endpoints, harvesting sensitive information without user awareness.
Once obtained, stolen data is trafficked on dark-web marketplaces, where it underpins subsequent malicious activities such as identity theft and financial exploitation.
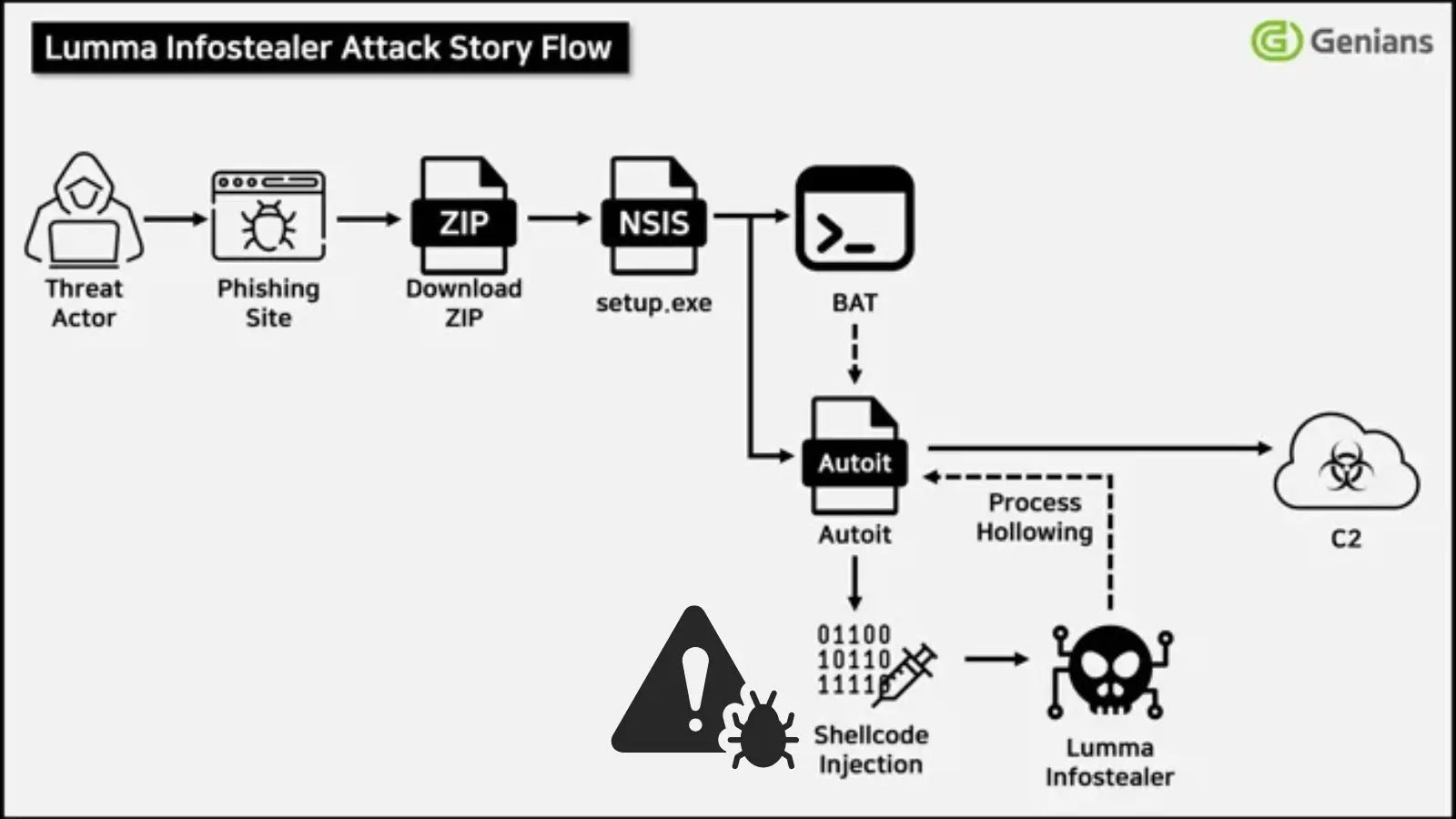
Genians Security Center (GSC) has identified Lumma Infostealer, a malware packaged and distributed using Nullsoft Scriptable Install System (NSIS).


Organized cybercrime groups deployed infostealers not just as standalone threats but as precursors to sophisticated attacks like ransomware and account takeovers—escalating the urgency for robust detection mechanisms.
Malware-as-a-Service (MaaS) Ecosystem
Malware-as-a-Service enables attackers to rent or subscribe to fully managed malware platforms. Luma Infostealer exemplifies this model, offering easy accessibility via dark-web channels and modular customization of payloads and command-and-control (C2) connection methods.
MaaS providers maintain development, infrastructure, and updates, while users—regardless of technical skill—execute campaigns and resell stolen data.
This model lowers barriers to entry for cybercrime, expands attack scale through affiliate networks, and complicates attribution as identical malware is deployed by multiple actors.
Since its debut in August 2022, Luma has been packaged using the Nullsoft Scriptable Install System (NSIS) and distributed via phishing sites masquerading as cracked software.


Analysis by Genian Security Center reveals a multi-stage infection chain: NSIS installers drop fragmented AutoIt modules, reassemble obfuscated shellcode in memory, and employ process hollowing to run the infostealer under the guise of legitimate processes.
Frequent updates and variable distribution URLs thwart traditional signature-based detection, underscoring the need for behavior-based EDR.When you download a file from the above site, a password-protected ZIP file will be saved.


Attackers direct victims through redirection sites to cloud storage platforms like MEGA, leveraging legitimate services to bypass IP and domain filters.
The downloaded NSIS package contains a password-protected ZIP, which unpacks “setup.exe.”
The ‘Contribute.docx’ file contains dummy code and obfuscated cmd commands.


Execution of this installer triggers a series of scripted steps—file drops, security-process checks using tasklist and findstr, CAB extraction, and recombination of AutoIt payloads—all culminating in execution of the malicious script.
Luma then decrypts its embedded C2 domains (e.g., rhussois[.]su, diadtuky[.]su), exfiltrates browser credentials, Telegram data, cryptocurrency keys, and remote access credentials.
Mitigations
Traditional antivirus solutions struggle to detect Luma’s obfuscation and process injection techniques. In contrast, modern EDR platforms excel at identifying suspicious behaviors—such as in-memory shellcode execution, unusual process hollowing events, and repeated redirection to unknown C2 domains.
Next, we use ‘extrac32.exe’ to extract the CAB file disguised as ‘Make.docx’. This CAB file contains 11 files, which will be used later to generate the AutoIt program.


Integrating real-time threat intelligence enables security teams to correlate emerging indicators and adapt detection rules swiftly.
Additionally, organizations should enforce multi-factor authentication for all critical accounts, discourage credential storage in browsers, and monitor network anomalies indicative of lateral movement or data exfiltration.
Luma Infostealer demonstrates how MaaS offerings can democratize sophisticated attack capabilities, placing high-value credentials at risk and facilitating larger attack chains, including ransomware and network infiltration.
To counter these threats, organizations must adopt EDR solutions capable of behavior-based detection, leverage threat intelligence feeds, and implement strict authentication and monitoring policies.
By focusing on the detection of anomalous endpoint behaviors and continually updating defense strategies, security teams can thwart Luma-driven attacks and protect sensitive assets from exploitation.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.