Cybersecurity researchers have uncovered a sophisticated malware campaign targeting Brazilian users through WhatsApp, delivering a dangerous new banking Trojan dubbed “Maverick.”
The threat has already blocked over 62,000 infection attempts in Brazil during the first 10 days of October alone, demonstrating its massive scale and potential impact.
The attack begins when victims receive a malicious ZIP file containing an LNK file through WhatsApp messages. These files often masquerade as legitimate bank documents with Portuguese-language filenames to appear trustworthy.
The messages typically instruct recipients to view the file on a computer and bypass Chrome’s security warnings by selecting “keep file.”
What makes this campaign particularly dangerous is its self-propagating nature. Once installed, Maverick utilizes WPPConnect, an open-source WhatsApp automation tool, to hijack victims’ accounts and automatically send the malicious files to their contacts through WhatsApp Web.
This worm-like behavior enables exponential spread across the platform, turning each infected user into an unwitting distributor of the malware.
The infection process is remarkably sophisticated and operates almost entirely in memory, leaving minimal traces on disk.
After the initial LNK file executes, it triggers a series of PowerShell scripts that download encrypted payloads from command-and-control servers.
The malware employs multiple verification layers, including User-Agent validation, to ensure downloads originate only from the malware itself, preventing security researchers from easily obtaining samples.
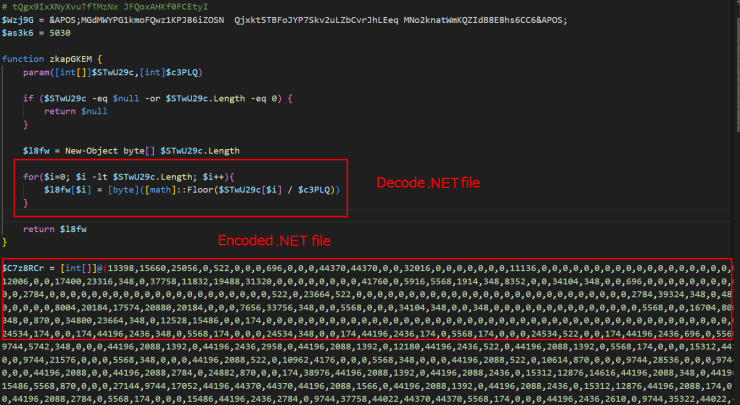

The entire operation uses modular components loaded through PowerShell, .NET assemblies, and Donut-encrypted shellcode.
Each stage downloads and decrypts the next, creating a complex chain that culminates in the deployment of the Maverick banking Trojan.
The malware specifically targets Brazilian users by checking the victim’s time zone, language settings, regional configuration, and date format before proceeding with installation.
Extensive Banking Capabilities
Notably, researchers found evidence that artificial intelligence was used in Maverick’s development, particularly in certificate decryption routines and general code structure.
To communicate with its API, it sends the API key in the “X-Request-Headers” field of the HTTP request header.
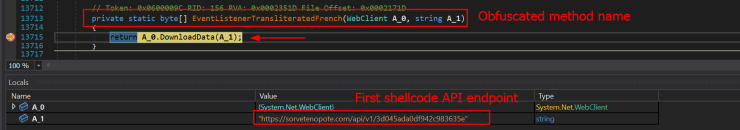

Once active, Maverick monitors victims’ browsers for access to 26 Brazilian banking websites, six cryptocurrency exchanges, and one payment platform.
The Trojan supports major browsers including Chrome, Firefox, Microsoft Edge, Brave, and Internet Explorer.
The malware’s capabilities are comprehensive and alarming. It can capture screenshots, log keystrokes, control the mouse, monitor browsing activity, terminate processes, and display overlay phishing pages when victims access banking websites.
These features enable attackers to capture banking credentials and perform unauthorized transactions while maintaining complete remote control over infected computers.
Security researchers identified significant code overlaps between Maverick and another Brazilian banking Trojan called Coyote, which was documented in early 2024.
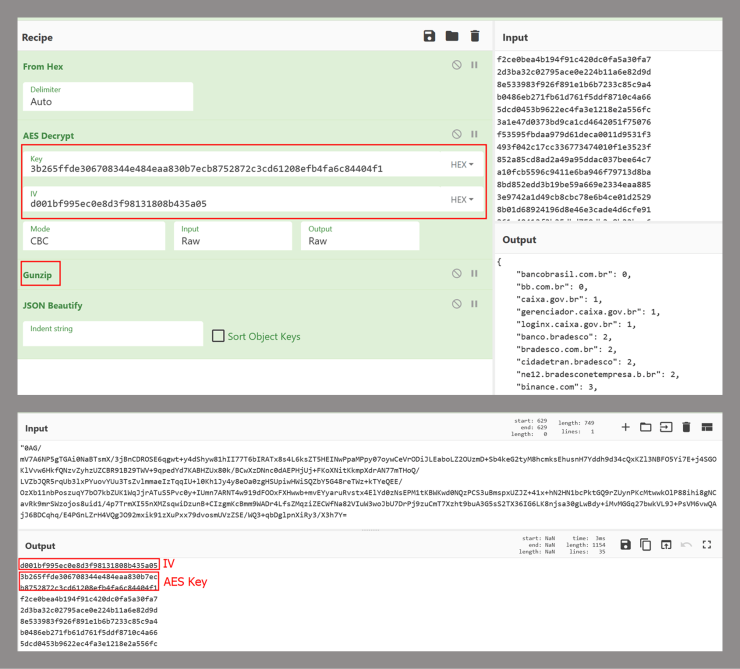

Both threats share similar encryption mechanisms using AES-256 and employ comparable communication protocols. However, Maverick’s architectural differences suggest it represents either a complete refactoring of Coyote or a new threat developed using shared code libraries.
Protection Recommendations
This marks a concerning evolution in malware development, where threat actors leverage AI tools to create more sophisticated threats.
Users should remain vigilant about unsolicited files received through WhatsApp, even from known contacts whose accounts may be compromised.
Organizations should implement email and messaging security solutions capable of detecting malicious LNK files, maintain updated antivirus software, and educate users about the risks of downloading and executing files from messaging platforms.
Brazilian banking customers should be particularly cautious and verify any suspicious banking-related messages through official channels before taking action.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.


