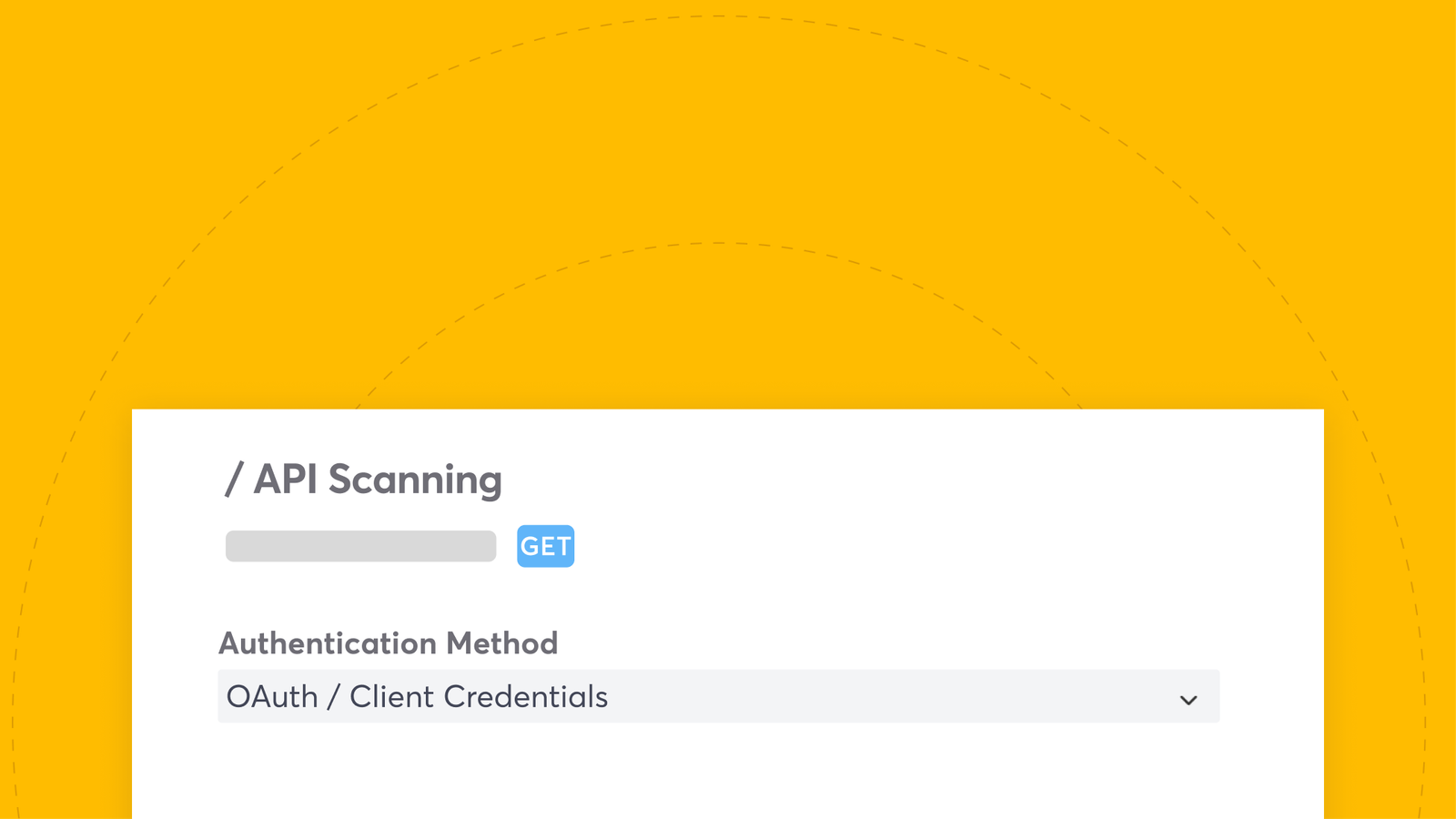
Our API scanner can test for dozens of vulnerability types like prompt injections and misconfigurations. We’re excited to share today that we’re releasing vulnerability tests for OAuth API authorization for organizations that use JWT tokens. These JWT, or JSON Web Tokens, are meant to prove that you have access to whatever it is you are accessing. One of the most critical JWT vulnerabilities is algorithm confusion. This occurs when an attacker tricks the server into verifying the token’s signature using a different, less secure algorithm than intended. There are plenty of other issues that can go wrong with managing JWT, which is why having a test to catch these misconfigurations is so useful.
Our API scanner can now detect a variety of misconfigurations that occur with JWT, like timestamp confusion or even manipulating the header with ‘none.’ This will help mitigate the risk of misconfigurations that come up when things like managing complex infrastructure is a daily part of an AppSec team’s scope.
So, how are we able to release new types of vulnerability tests that are outside of the OWASP API Top Ten or publicly available CVEs?
When we set out to build our API scanning engine, we faced a fundamental choice: wrap an existing open-source tool like ZAP, or build something from the ground up. Unlike other vendors, we chose the latter. While open-source tools are invaluable to the security community, we believe our customers deserve more than repackaged checks and noisy results. To deliver on that, we engineered a proprietary engine guided by three core principles:
- Dynamic Payloads. Traditional API scanners run the same tests, and if your API hasn’t changed, you get the same results. This can create a false sense of security. We’ve taken a different approach. Our engine uses dynamic payloads that are randomized and rotated with every scan. This means that each scan is a unique event, a novel attempt to find vulnerabilities that static checks would miss. Even in an unchanged API, our scanner offers a continuous opportunity for discovery.
- Massive Scale, Reproducible Results. Our dynamic approach doesn’t come at the cost of consistency. It allows for a massive scale of test variations. For certain tests, like prompt injection, the number of potential payload permutations is theoretically over 922 quintillion. For command injections, we draw from a library of over 330,000 payloads. This isn’t chaos; it’s controlled and predictable randomization. We use a “seed” for each scan, much like a seed in Minecraft generates a specific world. This allows us to precisely reproduce the exact payload that identified a vulnerability, ensuring our findings are always verifiable and actionable for your developers.
- Research-Led, High-Fidelity Findings. Our engine is the product of our internal security research team—the same team that powers the rest of Detectify. We prioritize exploitability, meaning we attempt to actually exploit a vulnerability rather than simply flagging a potential issue. This, combined with our proprietary fuzzing technology with a history of finding zero-days, results in high-accuracy findings you can trust. This drastically reduces the time you would otherwise waste on triaging false positives, allowing you to focus on what matters.
Research-led vulnerability testing means that our engines don’t rely on publicly available information.
Detectify builds and maintains its scanning engines in-house to tailor them specifically for modern application architectures. This approach is designed to yield more accurate results for custom applications by better understanding complex logic and API-driven front-ends. In contrast, general-purpose open-source engines can struggle with the nuances of modern apps and APIs.
Why does this matter to AppSec teams? Simply put, reduced noise. Many security vendors today rely heavily on open-source tooling, meaning no steps are taken by the tool to reduce noise. By building its own engines, Detectify can implement methodologies like testing for OAuth authorization, which helps curb the time users spend validating vulnerabilities.
This means that our API Scanner is not only dynamic in how it tests for vulnerabilities, but also not limited by what is possible at the moment
One piece of feedback we’ve regularly received from our customers is that they find the breadth of coverage really useful. Not only can we discover high and critical vulnerabilities, but we can also find issues like misconfigured JWT tokens and missing security headers, something that isn’t commonly available in API scanners.
We can deliver this kind of experience to our users because our engines are built with the AppSec team in mind, meaning that we consider the use cases that our users need.
Detectify’s research-led approach and proprietary fuzzing engine deliver high-fidelity, actionable results that empower AppSec teams to secure their APIs with confidence – try our API scanner to experience the difference.