The Acronis Threat Research Unit (TRU) has uncovered a sophisticated malware campaign deploying infostealers like Leet Stealer, its modified variant RMC Stealer, and Sniffer Stealer, leveraging social engineering tactics centered on gaming hype.
These threats masquerade as indie game installers, such as Baruda Quest, Warstorm Fire, and Dire Talon, promoted via fraudulent websites and fake YouTube channels and primarily distributed through Discord.
Attackers exploit stolen branding from legitimate titles like Club Cooee, Crossfire: Sierra Squad, and Project Feline to create convincing lures, tricking users into downloading executables that harvest browser credentials, Discord tokens, and other sensitive data.
Indie Game Impersonation
The campaign’s impact is profound, enabling attackers to impersonate victims for further malware propagation, extortion, or financial scams, often resulting in account takeovers, monetary losses, and emotional distress.
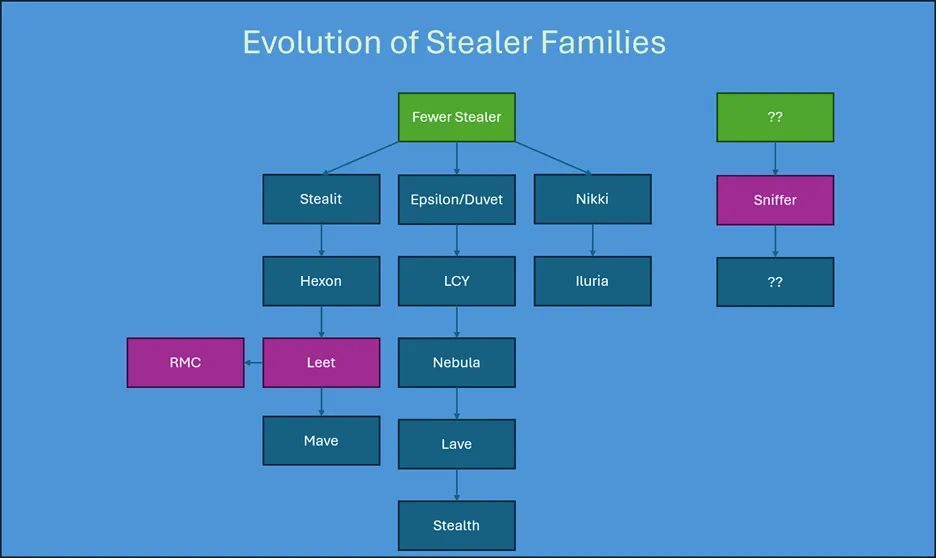
Many of these stealers trace their lineage to Fewer Stealer, an foundational Electron framework-based tool that facilitates cross-platform desktop apps using JavaScript, HTML, CSS, Node.js, and Chromium.
Leet Stealer, introduced in late 2024 as a Malware-as-a-Service (MaaS) with subscription tiers starting at $30 monthly, features capabilities like credential exfiltration and token grabbing.
Its source code was sold in April 2025 alongside Hexon Stealer, leading to derivatives like RMC Stealer and potentially Mave Stealer, while Sniffer Stealer appears independently developed without clear forks.

Campaign operators enhance credibility by crafting dedicated promotional assets, including YouTube videos and multilingual websites (often defaulting to Portuguese, indicating possible Brazilian origins), with download links redirecting to malware-laden files hosted on Discord CDN or Dropbox.
In-Depth Technical Analysis
For instance, Baruda Quest’s site offered Windows, Android, and macOS downloads, but only the Windows executable deployed RMC Stealer, while others linked to benign games.
Warstorm Fire and Dire Talon variants used password-protected RAR archives containing Sniffer Stealer, with no actual game content instead relying on fake error messages to dismiss installation failures as hardware incompatibilities.
VirusTotal telemetry shows heavy submissions from Brazil and the U.S., underscoring Discord’s role in global dissemination amid gaming communities.
Technically, these Electron-packaged samples, often bundled via Nullsoft Scriptable Install System (NSIS), embed malicious JavaScript in app.asar archives, which can be extracted using tools like 7-Zip and Node.js’s asar utility.
According to the Report, A notable operational blunder in a Baruda Quest sample left unobfuscated source code exposed, revealing RMC Stealer’s sandbox evasion tactics: blacklisting IPs, hostnames, usernames, GPUs, and processes via WMIC queries, plus RAM checks below 2GB to detect virtual environments.
Upon evasion failure, it displays deceptive VBScript error popups. Successful execution targets browsers (Chrome, Edge, etc.) by running them in debug mode to extract cookies, passwords, and form data, zipping and exfiltrating via services like gofile.io or alternatives.
It also harvests Discord tokens for account hijacking, alongside data from Steam, Growtopia, Minecraft, Epic Games, WhatsApp, Telegram, and BetterDiscord, with capabilities to download additional payloads.
Multilingual code comments (Portuguese, Turkish, and English) suggest collaborative modifications. Acronis Cyber Protect Cloud detects and blocks these threats, highlighting the blend of technical sophistication and psychological manipulation in modern stealers.
This campaign exemplifies the evolution of malware from pure code exploits to integrated social engineering, exploiting platforms like Discord and YouTube to target gamers and harvest credentials at scale.
Indicators of Compromise (IoC)
| Filename | Stealer Family | SHA256 |
|---|---|---|
| babacan32 Setup 1.0.0.exe | Leet | 5c7c70ab9734838795050a91f08f1af9e3cb479caf20bd34944282e8ac455ea7 |
| BarudaQuest.exe | RMC | 813e5923e6d4df56055f5b5200db2e074e89f64dea3099e61fbde78c0fc23597 |
| damnedbetter.exe | Sniffer | 150f7b4615a2e0e7d21a32e12e796fc009c1fe25f2efff889acf84924fef39e4 |
| damnedbetter.exe | Sniffer | 321c7c999ecc5670207394f2f2d3cf4712b15f1f87c1b0ec05ed2367d922f1dc |
| Denemeamacimiz Setup 1.0.0.exe | Leet | 82421012c689dfe36965d5c89bbeb4af3efb65556eb8df4bf5b863e261e28e8b |
| Depthcan.exe | Leet | 798eee15a3e93ee0d261501df979dc3b61a9e5992188edeada5beaba0b30b8df |
| DireTaloGaSetup.exe | Sniffer | 35ad1623694496ec91bc853b391c8bebdfa1aeaea2c4dcf74516e2cd13ab44f4 |
| Dire Talon.exe | Sniffer | 58d8a8502e7e525795cd402c7d240b50efcdde449eab9ee382f132f690a1989c |
| EdensGameInstall.exe | Sniffer | 8294f79f9ecf81a65cdc049db51a09cd352536d7993abd0cfa241bbbceefa6e3 |
| emeraltfates.exe | Sniffer | b127202d13bd170c15c3733991d790bc5464e3d77965e9cf59172c7cf3881738 |
| Jorosa Setup 1.0.0.exe | Leet | a07462af74cdccc1bba698aa5175923437d400c87e0b88601414630f7ee08f97 |
| Lacrimos.exe | Sniffer | 1ca60801bed5f8a607afb7054536bdd7d56670c04d3836cdf0cd4e07d8f2edff |
| Salonca Setup 1.0.0.exe | Leet | 9411b71653f83190a139296d58737f3935bdd58c13142381e59a8d106184e15e |
| slenderthreads.exe | Sniffer | d33dbba2f4e25148e2d9a59b1157d71d29ab5a30beeb5f0992b0d3f2859a90c2 |
| Sokakcan.exe | Leet | a3636b09302a77ed7a6c75c5e679ba9ed0dbe12892f5fe94975ab3ef6be7ade8 |
| Terrnua Setup 1.0.0.exe | Leet | 767f575d30deb66244b29bafae51111fdb869ba26d1df902e3f839bdb64725f9 |
Get Free Ultimate SOC Requirements Checklist Before you build, buy, or switch your SOC for 2025 - Download Now



