CyberProof researchers detected a significant surge in Remcos (Remote Control & Surveillance Software) campaigns throughout September and October 2025, exploiting sophisticated fileless techniques to evade endpoint detection and response (EDR) solutions.
By leveraging highly obfuscated PowerShell scripts and process hollowing into Microsoft’s RMClient.exe, attackers are gaining stealthy persistence and targeting browser credentials.
Although Remcos is advertised as a legitimate commercial remote access tool for surveillance and penetration testing, threat actors continue to repurpose it for illicit operations.
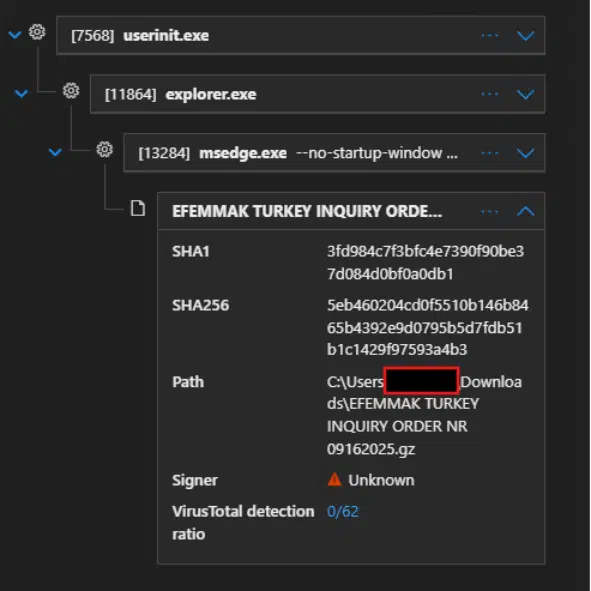
The recipient, enticed by a credible “inquiry order” theme, downloaded the file via Microsoft Edge. Once extracted, the archive dropped a batch file under the user’s Temp directory with a path resembling:
C:\Users

This batch file launched an obfuscated PowerShell script using functions dubbed ‘Lotusblo’ and ‘Garrots’ to conceal its true purpose.
Dynamic Payload Retrieval
The embedded PowerShell code spawned a hidden process, employed a bespoke string de-obfuscator, and invoked downloaded payloads dynamically with Invoke-Expression.
Configured to enforce TLS 1.2 and use a custom User-Agent, the script targeted C:\Users
Upon download, the file underwent Base64 decoding, GZip decompression, and execution via Invoke-Expression.
In the most recent incident, the attack commenced with a spear-phishing email containing an archive named “EFEMMAK TURKEY INQUIRY ORDER NR 09162025.gz.”
A subsequent PowerShell snippet leveraged msiexec.exe to execute the next stage:
powershellpowershell.exe -windowstyle hidden "spsv exergonic; function Lotusblo ...
Garrots (Lotusblo '…')"
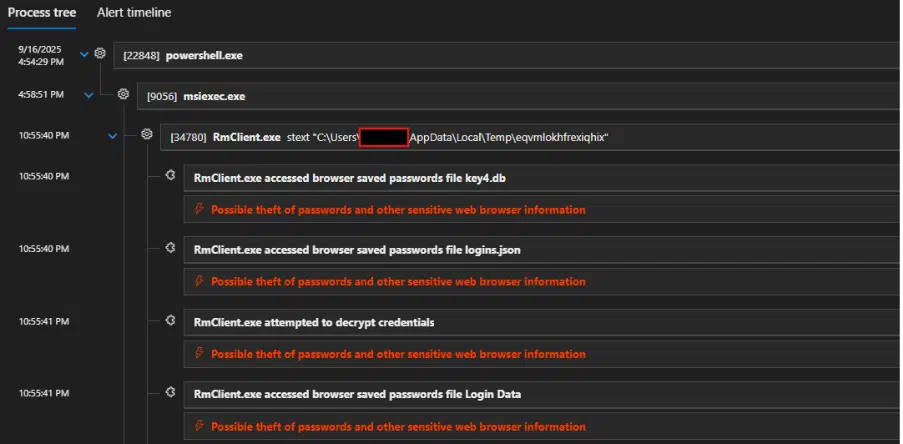
This command concealed malicious parameters and executed msiexec.exe, which in turn hollowed its own memory to host the Remcos payload within RMClient.exe.

The fileless approach exploited the legitimate RMClient binary—whose SHA-256 hash ‘8f6a3b111f6e0498cb677b175966175bfa53e58c9fb41ddb63c7b7568e24c760’ matches the authentic Microsoft distribution—to mask malicious activity.
EDR systems partially detected anomalous behavior when msiexec.exe attempted process hollowing into RMClient.exe, triggering alerts as the RAT probed browser password storage files.
CyberProof analysts identified that the injected Remcos instance actively accessed saved credentials within Chromium-based browsers, indicating a primary motive of credential theft through opportunistic targeted attacks.
Post-injection, analysis of msiexec’s process ID revealed the creation of randomly named files in the Temp directory and multiple command-and-control (C2) communications.

Initial C2 connections to domains such as icebergtbilisi.ge succeeded before subsequent attempts failed. Network forensics confirmed GET requests to malicious endpoints using the custom User-Agent string embedded in the PowerShell loader.
Monitoring and Hunting
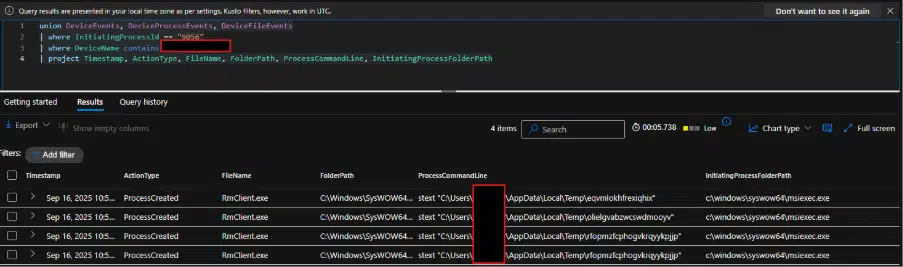
To assist defenders, CyberProof researchers shared a Kusto Query Language (KQL) hunting query to capture related events:
textunion DeviceEvents, DeviceProcessEvents
| where FileName contains "rmclient.exe"
| where ProcessCommandLine contains "AppData\\Local\\Temp"
| project Timestamp, FileName, FolderPath, ProcessCommandLine, InitiatingProcessFileName, InitiatingProcessParentFileName
This query isolates instances of RMClient.exe launched by msiexec from temporary folders, effectively highlighting potential fileless Remcos infections.
CyberProof continues to monitor this evolving campaign. Initial assessments suggest that attackers may have compromised legitimate websites to host additional payloads.
As the fileless methodology renders traditional signature-based detection less effective, organizations are urged to bolster behavioral monitoring, enforce strict PowerShell execution policies, and employ real-time memory scanning to detect anomalous process hollowing and dynamic code execution. Updates to detection rules and threat intelligence feeds will be published as new indicators emerge.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.



