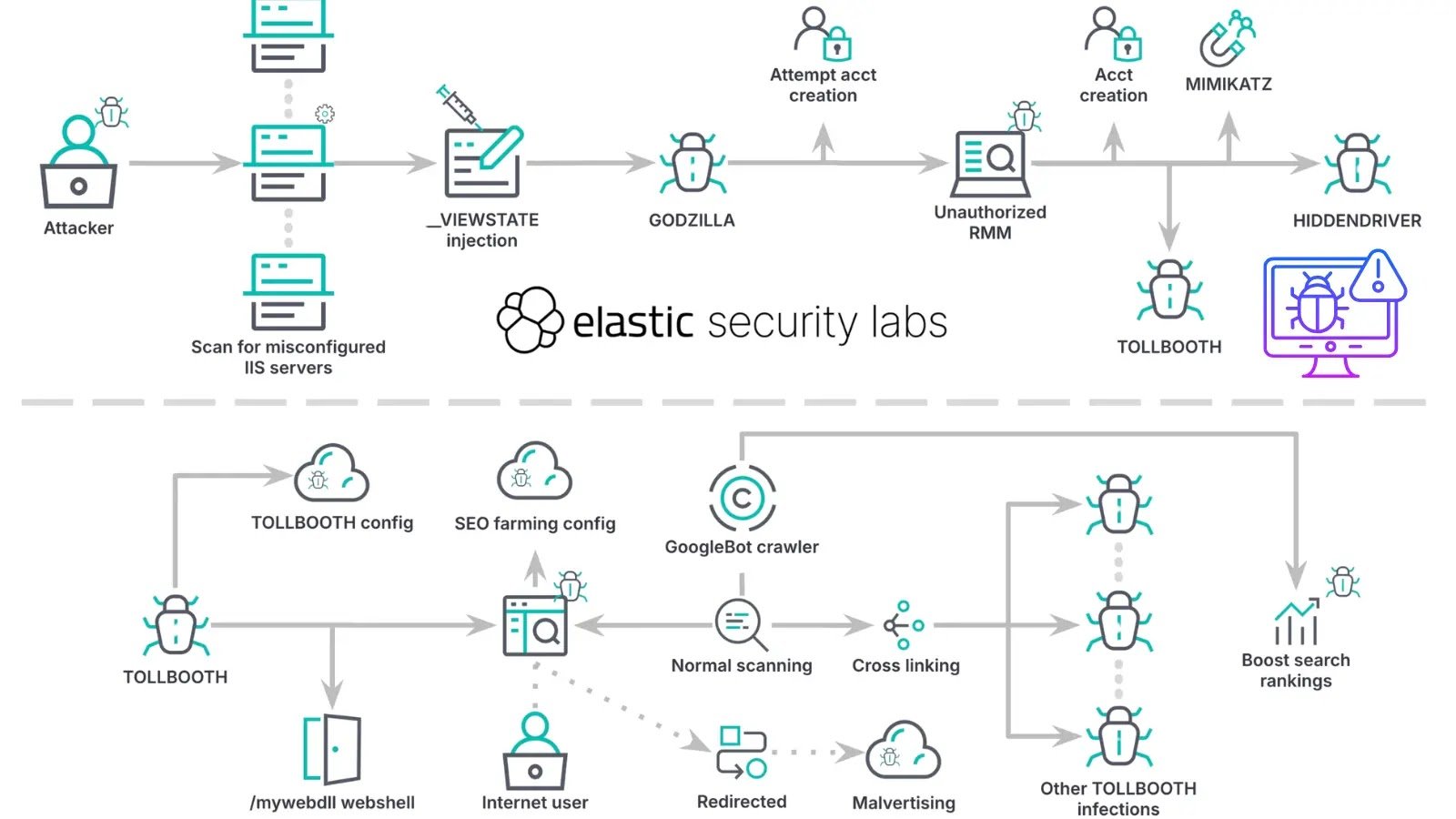
In September 2025, Texas A&M University System (TAMUS) Cybersecurity, a managed detection and response provider, in collaboration with Elastic Security Labs, uncovered a sophisticated post-exploitation campaign by a Chinese-speaking threat actor.
Using this method, the attackers installed a malicious IIS module named TOLLBOOTH, deployed a Godzilla-forked webshell framework, leveraged the GotoHTTP remote monitoring and management tool, and introduced a kernel-mode rootkit to conceal their presence.
This cluster, designated REF3927, represents a global campaign that has already impacted hundreds of servers across multiple industries.
The initial compromise stemmed from deserialization attacks against the ASP.NET ViewState mechanism. ASP.NET machine keys—comprising the ValidationKey and DecryptionKey—are used to protect ViewState and authentication cookies.
The group exploited misconfigured IIS web servers that reused ASP.NET machine keys publicly published in resources such as Microsoft documentation and StackOverflow.
When these keys are exposed, an attacker can forge serialized payloads that execute arbitrary code upon deserialization.
In our analysis, a POST request containing a Base64-encoded, ViewState payload generated by the open-source ysoserial.net tool successfully triggered code execution, resulting in an HTTP 500 Internal Server Error on vulnerable servers.
Last month, Elastic Security Labs and Texas A&M System Cybersecurity investigated an intrusion involving a misconfigured Windows IIS server.


This method mirrors earlier reports by Microsoft in February and by AhnLab in April, suggesting REF3927 is an evolution of the same malicious chain.
Post-Compromise Activity and Tooling
Following initial access, the threat actor deployed multiple persistence and evasion tools. A Godzilla-forked webshell framework, Z-Godzilla_ekp, provided in-memory assembly execution, AMSI bypassing, and encrypted communication disguised within HTTP POST parameters.
When attempts to create new Windows accounts failed, the actor installed the legitimate GotoHTTP RMM tool to maintain control, routing all management traffic through standard web ports. Efforts to dump credentials via Mimikatz were thwarted by Elastic Defend’s endpoint protections.


When interactive escalation was blocked, the group deployed TOLLBOOTH, a traffic-hijacking IIS module available in both native and .NET managed variants.
TOLLBOOTH dynamically retrieves per-victim configuration files from attacker-controlled infrastructure, implements SEO cloaking to inflate search engine rankings, and exposes a hardcoded webshell at /mywebdll.
The module partitions behavior between search crawlers and human visitors, serving keyword-stuffed link farms to bots and redirecting users to malicious landing pages.
To prepare its internal components before populating its driver object and associated fields, such as major functions.


Administrators also discovered attempts to load a modified version of the open-source Hidden rootkit, dubbed HIDDENDRIVER, which uses Direct Kernel Object Manipulation (DKOM) and registry-based configuration flags to hide files, processes, and registry keys.
Collaboration with Validin, leveraging its global scanning infrastructure, identified 571 active TOLLBOOTH infections worldwide. Victims spanned multiple geographies and industry verticals, indicating an untargeted, automated exploitation strategy.
It searches for the PspCidTable address by disassembling the function PsLookupProcessByProcessIdwith the library Zydis and parsing it.


Notably, no victims were found within mainland China, reflecting a self-imposed geofencing tactic. Repeated reinfections on remediated servers highlight the importance of rotating exposed machine keys in addition to cleaning malicious artifacts.
Remediation requires a two-fold approach: first, restore affected servers to a known-good state by removing malware, modules, and rootkits; second, generate and configure new, cryptographically secure ASP.NET machine keys via tools like IIS Manager.
Organizations are advised to audit their IIS configurations for reused machine keys, enable robust ViewState validation, and deploy endpoint detection solutions to alert on kernel driver loads and unauthorized module installations.
The REF3927 campaign underscores how a simple configuration error can cascade into full server compromise.
By integrating open-source tooling, legitimate RMM software, and custom kernel drivers, attackers have crafted an effective and evasive intrusion set.
Defenders of publicly exposed IIS environments must prioritize secure machine key management, continuous monitoring of ViewState integrity, and hardened endpoint defenses to thwart similar exploits in the future.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.