DShield honeypots have reported previously unheard-of log quantities in a startling increase in cyber reconnaissance activity, with some subnets producing over a million entries in a single day.
This surge, observed across multiple honeypot instances including residential and archived setups, marks a departure from historical patterns where high-activity spikes were rare anomalies.
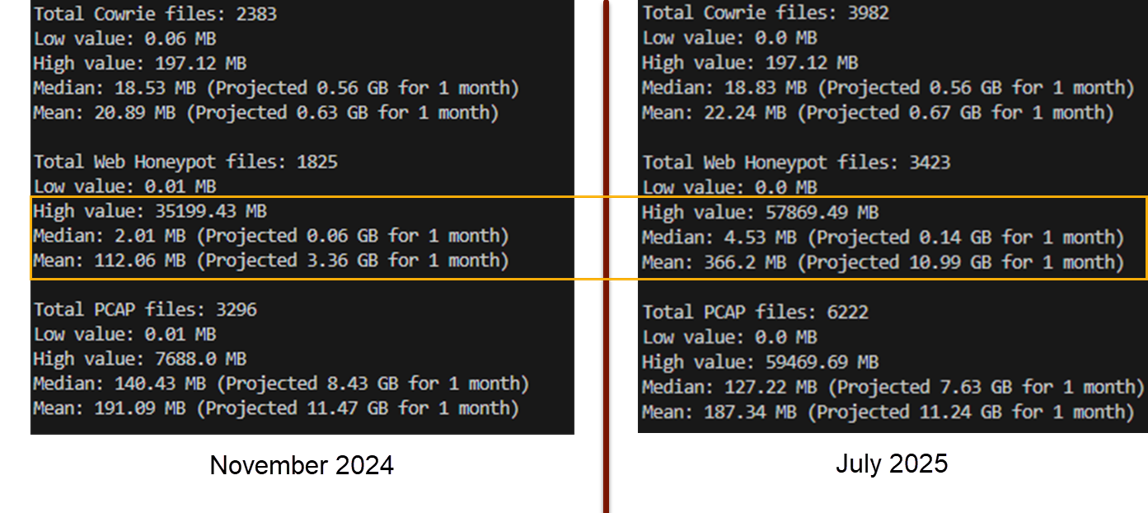
Over the past few months, particularly since April 2025, web honeypot logs have dominated this influx, often exceeding 1 GB daily and peaking at nearly 58 GB in one instance surpassing previous records of around 35 GB.
Unprecedented Surge in Web Honeypot Activity
Such volumes not only strain storage resources but also highlight intensified internet-wide scanning and potential malicious probing.
Analysis of 13-14 months of data reveals that recent activity has overshadowed earlier logs, rendering them nearly invisible in unfiltered visualizations.
When filtering out source networks (/24 subnets) contributing more than 1 million logs per day, underlying patterns emerge, showing a persistent uptick in baseline activity even prior to the recent peaks.
According to the Report, this filtered view underscores that while anomalous high-volume days occurred sporadically in the past, the current frequency and magnitude are exceptional, with multiple honeypots logging over 20 GB daily for consecutive periods.
Technically, this phenomenon is driven by automated scanning from overlapping subnets, targeting specific URL paths indicative of vulnerability probing or reconnaissance.
Subnets like 45.146.130.0/24 have amassed over 200 million hits, primarily from a handful of IPs focusing on root paths (“/”), while others such as 179.60.146.0/24 concentrate on API endpoints like “/api/v1/config/domains”.
The diversity in unique IP counts and URL paths per subnet suggests coordinated botnet-like operations, potentially scanning for misconfigurations in web services, domain APIs, or even SSL VPN endpoints.
For instance, subnets with low unique URL diversity, such as those hitting only 2-3 paths, point to targeted campaigns, whereas broader explorations (e.g., up to 18,152 unique paths in 80.243.171.0/24) indicate opportunistic enumeration.
The most common paths across these subnets include the root “/”, accounting for over 38 billion hits, and “/api/v1/config/domains” with 33 billion, followed by “/api/v1/logon” at 1.6 billion.
Less frequent but notable are queries to external services like “api.ipapi.is:443” and “myip.wtf:443”, which may relate to IP geolocation or self-identification in scanning tools.
This data, aggregated from raw logs, illustrates a shift toward more aggressive web-based reconnaissance, possibly exploiting unpatched servers or gathering intelligence for future exploits.
Implications for Honeypot Operators
The escalating log volumes necessitate proactive measures for honeypot maintainers, including frequent archiving with high-compression techniques like twice-daily zipping to manage storage demands.
With potential weekly accumulations exceeding 140 GB for web logs alone, operators must enhance backup protocols to prevent data loss or resource exhaustion.
This trend could signal broader cyber threats, urging security teams to monitor similar indicators in production environments.
Deeper forensic analysis of these logs may reveal evolving tactics, techniques, and procedures (TTPs) in adversary behavior, such as subnet-based coordination for evading detection.
This record-breaking activity in DShield honeypots underscores a new era of persistent, high-volume scanning, demanding adaptive responses from the cybersecurity community to mitigate associated risks.
Stay Updated on Daily Cybersecurity News. Follow us on Google News, LinkedIn, and X.