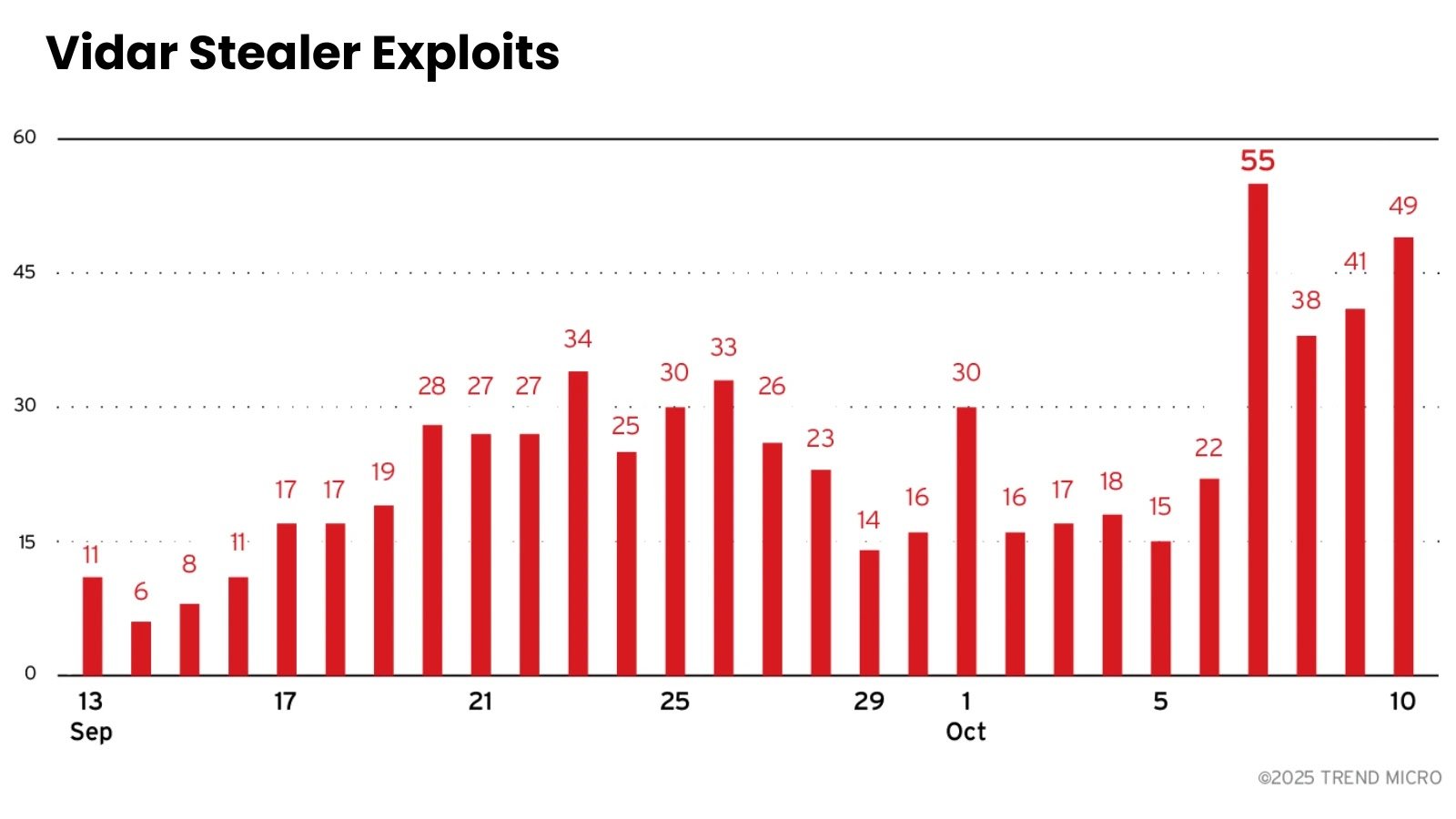
On October 6, 2025, the cybercriminal developer known as “Loadbaks” announced the release of Vidar Stealer v2.0 on underground forums, introducing a sophisticated information-stealing malware that employs direct memory injection to bypass modern browser security protections.
This new version represents a complete architectural overhaul, transitioning from C++ to a pure C implementation that allegedly enhances performance and stealth capabilities.
The release comes amid declining activity surrounding the Lumma Stealer, suggesting cybercriminals are actively seeking more effective alternatives in the evolving threat landscape.
Vidar 2.0 introduced several concerning features including advanced anti-analysis measures, multithreaded data theft capabilities, and sophisticated methods for extracting browser credentials that can defeat Chrome’s latest AppBound encryption protections.
With a lifetime price of just $300, the malware offers attackers powerful credential-stealing tools that are both cost-effective and technically advanced, positioning it as a significant threat to organizations and individual users alike.
Vidar first emerged in 2018 on Russian-language underground forums, initially leveraging the Arkei stealer source code.


Over seven years, it has distinguished itself from competitors like Raccoon and RedLine through consistent updates, reliable developer support, and comprehensive data-stealing capabilities targeting browser credentials, cryptocurrency wallets, and two-factor authentication applications.
The October 2025 release of version 2.0 represents the most significant technical evolution in the malware’s history, addressing previous limitations while introducing capabilities specifically designed to bypass modern security protections.
Advanced Memory Injection Techniques
The most notable advancement in Vidar 2.0 is its sophisticated approach to bypassing Chrome’s AppBound encryption, a security feature designed to prevent unauthorized credential extraction by binding encryption keys to specific applications.
According to the developer, Vidar 2.0 implements “unique appBound methods that aren’t found in the public domain,” representing a significant escalation in information stealer capabilities.

Binary analysis reveals that the malware employs a multi-stage credential extraction process. Initially, Vidar attempts traditional methods including systematic enumeration of browser profiles and extraction of encryption keys from Local State files using standard DPAPI decryption.
However, when these conventional approaches fail against modern browser protections, the malware escalates to advanced techniques that fundamentally change how credential theft occurs.
The advanced technique launches target browsers with debugging enabled and injects malicious code directly into running browser processes using either shellcode or reflective DLL injection.


This injected payload extracts encryption keys directly from browser memory rather than attempting to decrypt them from storage, effectively bypassing Chrome’s AppBound encryption protections.
The stolen keys are then communicated back to the main malware process via named pipes, avoiding disk artifacts that could alert security software or leave forensic evidence.
Performance and Evasion Enhancements
Beyond its browser credential theft capabilities, Vidar 2.0 introduces significant architectural improvements designed to maximize efficiency while evading detection.
The malware implements a sophisticated multithreading system that automatically adjusts performance based on victim computer specifications, creating more worker threads on powerful systems and fewer threads on weaker machines.

This approach allows simultaneous data theft from multiple sources including browsers, cryptocurrency wallets, and files, significantly reducing the time the malware needs to remain active on compromised systems.
The malware also employs heavy control flow flattening obfuscation, implementing complex switch-case structures with numeric state machines that obscure the original program logic and make reverse engineering considerably more difficult.
An automatic polymorphic builder generates samples with distinct binary signatures, making static detection methods ineffective.
These evasion techniques, combined with comprehensive anti-analysis checks including debugger detection, timing verification, and hardware profiling, ensure the malware executes only on genuine victim systems rather than analysis environments.
As Lumma Stealer activity continues declining and cybercriminals migrate to alternatives, security teams should anticipate increased Vidar 2.0 prevalence through Q4 2025 and beyond.
The malware’s technical capabilities, proven developer track record since 2018, and competitive pricing position it as a likely successor to Lumma Stealer’s market dominance.
Organizations must ensure endpoint solutions are fully utilized and updated, while maintaining strong policies for credential management and user education to protect against this evolving threat.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.