Group-IB Threat Intelligence has uncovered a sophisticated phishing campaign orchestrated by the Iran-linked Advanced Persistent Threat group MuddyWater, targeting international organizations worldwide to gather foreign intelligence.
The campaign demonstrates the threat actor’s evolving tactics and enhanced operational maturity in exploiting trusted communication channels to infiltrate high-value targets.
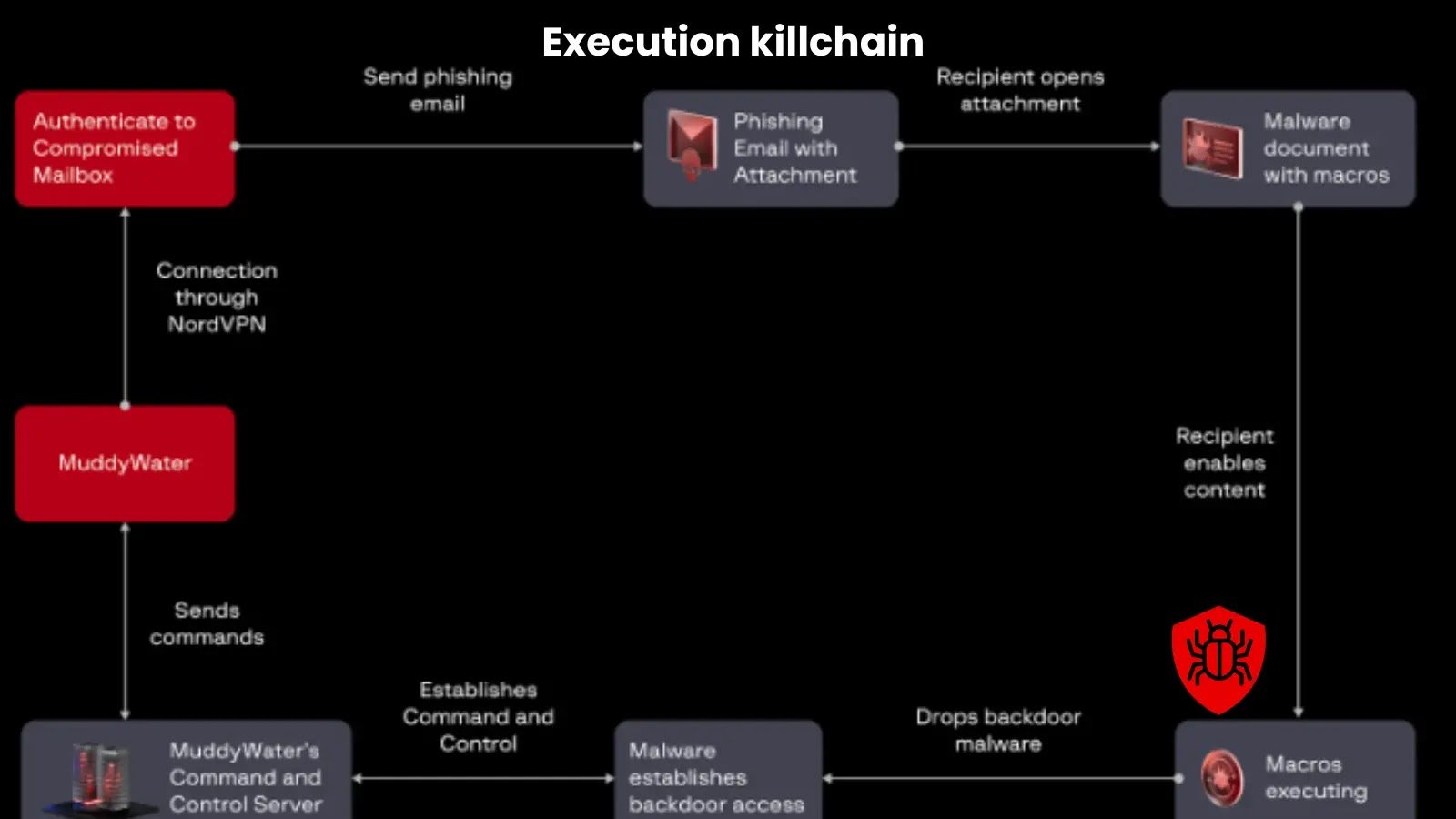
MuddyWater launched the operation by accessing a compromised mailbox through NordVPN, a legitimate service abused by the threat actor to mask their activities.
Using this compromised account, the group sent phishing emails that appeared as authentic correspondence from trusted sources.
By exploiting the authority and trust associated with such communications, the campaign significantly increased its chances of deceiving recipients into opening malicious attachments.
The phishing emails contained Microsoft Word documents that prompted recipients to enable macros to view blurred content.
Once macros were activated, the documents executed malicious Visual Basic for Application code, ultimately deploying version 4 of the Phoenix backdoor on victims’ systems.


This backdoor established continuous communication with command-and-control infrastructure, enabling remote control, data collection, and further post-exploitation activities.
High-Confidence Attribution
Group-IB attributes this campaign to MuddyWater with high confidence based on several indicators observed during investigation and analysis.
The dropped malware families—FakeUpdate injector and Phoenix backdoor—are custom malware previously observed exclusively in MuddyWater operations.
The malicious macro embedded in the documents shares similar logic with macros used in past MuddyWater campaigns.
Additionally, the command-and-control server hosts a custom browser credential stealer employing the same string decoding techniques observed in other MuddyWater-linked malware.
The same infrastructure contains PDQ RMM tools, which have been previously used by MuddyWater for remote access and persistence.
The targeting patterns align with MuddyWater’s historical victimology, specifically focusing on the Middle East region with expanding operations in Europe, Africa, and North America.
An examination of phishing email recipients reveals notable targeting patterns. The campaign included both official government accounts and personal email addresses from Yahoo, Gmail, and Hotmail, indicating MuddyWater possesses detailed knowledge of its targets.
The focus extended to influential global organizations engaged in international cooperation and humanitarian missions, highlighting the actor’s broader geopolitical motivations.


Group-IB identified additional malicious documents sharing technical and infrastructure overlaps with the current operation, suggesting continued activity involving related or concurrent campaigns.
One document impersonated a government organization seminar addressing ongoing geopolitical tensions, while another targeted the energy sector in the Middle East and North Africa.
During infrastructure investigation, Group-IB identified custom tools and remote monitoring management utilities hosted on the attacker’s command-and-control server.
The value of x-originating-ip in the email header is a NordVPN exit node located in France. The x-originating-ip header reveals the original IP address of the client or device that first submitted the email to the mail server.


These include a custom Chromium browser credential stealer disguised as a calculator application, along with Action1 and PDQ RMM utilities for remote management and command execution.
The credential stealer enumerates browser profile directories, extracts encryption keys, terminates active browser processes, and harvests stored login credentials from Google Chrome, Opera, Brave, and Microsoft Edge.
The stolen credentials are written to a staging file before the browser is restarted to minimize user suspicion.
Given MuddyWater’s sustained focus on governmental targets amid ongoing geopolitical tensions, Group-IB expects similar campaigns will continue, leveraging newly compromised accounts and evolving payloads.
The consistent pattern of reusing and modifying custom malware families underscores a long-term strategic intelligence objective.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.