A sophisticated spearphishing campaign has targeted humanitarian organizations working on Ukrainian war relief efforts, employing weaponized PDFs and fake Cloudflare captcha pages to deploy a custom remote access trojan.
The PhantomCaptcha campaign, launched on October 8th, 2025, specifically targeted individual members of the International Committee of the Red Cross, United Nations Children’s Fund (UNICEF) Ukraine office, Norwegian Refugee Council, and Council of Europe’s Register of Damage for Ukraine.
Ukrainian government administrations in the Donetsk, Dnipropetrovsk, Poltava, and Mikolaevsk regions also received malicious communications disguised as legitimate governmental documents.
SentinelLABS and the Digital Security Lab of Ukraine uncovered the coordinated attack, which impersonated the Ukrainian President’s Office to compromise critical aid organizations.
Threat actors distributed an eight-page weaponized PDF (SHA-256: e8d0943042e34a37ae8d79aeb4f9a2fa07b4a37955af2b0cc0e232b79c2e72f3) through emails impersonating Ukraine’s Presidential Office.
VirusTotal submissions revealed the malicious file was uploaded from multiple countries including Ukraine, India, Italy, and Slovakia, suggesting widespread targeting and potential victim interaction.
The embedded link within the PDF directed victims to zoomconference[.]app, a domain masquerading as a legitimate Zoom site but actually hosting a VPS server on Russian-owned infrastructure provider KVMKA.
Researchers discovered the malicious domain resolved to IP address 193.233.23[.]81 located in Finland and operated for only a single day before being taken offline, demonstrating sophisticated operational security.
Multi-Stage Social Engineering Attack
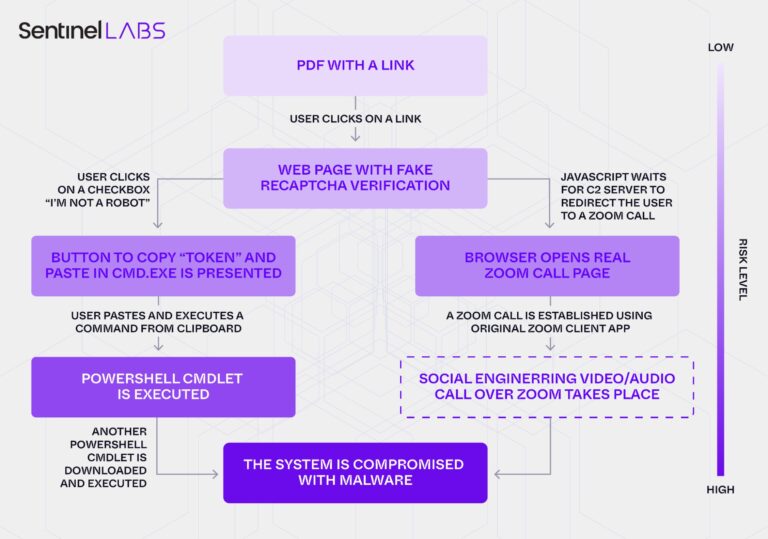
The campaign employed a variation of the “ClickFix” or “Paste and Run” social engineering technique that has proliferated since mid-2024.
After accessing the fake Zoom site, victims encountered a convincing counterfeit Cloudflare DDoS protection gateway that attempted establishing WebSocket connections to the attackers’ server.
![Initial view of a page from zoomconference[.]app.](https://www.sentinelone.com/wp-content/uploads/2025/10/PhantomCaptcha_4-1536x1037.jpg)
![Initial view of a page from zoomconference[.]app.](https://www.sentinelone.com/wp-content/uploads/2025/10/PhantomCaptcha_4-1536x1037.jpg)
When victims clicked the simulated reCaptcha “I’m not a robot” checkbox, a popup appeared with instructions in Ukrainian directing them to copy a token, press Windows + R to open the Run dialog, and paste the command.
This technique proved particularly effective because victims themselves executed the malicious code, bypassing traditional endpoint security controls focused on detecting malicious files.
The malware delivery occurred through three distinct stages. An initial heavily obfuscated PowerShell script exceeding 500KB downloaded a second-stage payload that performed system reconnaissance, collecting computer names, domain information, usernames, and system UUIDs.
This data was XOR-encrypted using a hardcoded key and transmitted to the command-and-control server.
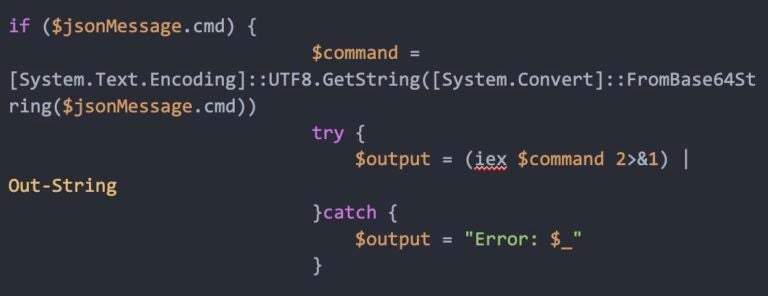

The final payload deployed a lightweight PowerShell backdoor establishing persistent WebSocket connections to wss://bsnowcommunications[.]com:80.
This WebSocket-based RAT enabled arbitrary remote command execution, data exfiltration, and potential deployment of additional malware on compromised systems.
Extended Infrastructure and Mobile Threats
Analysis revealed the attackers began preparing their infrastructure in March 2025, with the earliest related domain goodhillsenterprise[.]com registered on March 27th.
The domain’s content and the APK are themed around an adult entertainment venue in Lviv, Ukraine, called Princess Men’s Club. Similar APKs can be found in other themes as well, such as “Cloud Storage”.

SSL certificates were issued in September, and internal timestamps from the lure PDF dated back to August 2025 but were updated immediately before the October attack.
Infrastructure pivots uncovered an additional mobile attack vector featuring fake Android applications themed around Ukrainian businesses.
The malicious APK collected extensive device data including contacts, call logs, installed applications, location data, gallery images, and network information, transmitting everything to hardcoded command-and-control servers.

SentinelLABS identified potential overlaps with COLDRIVER, a Russian FSB-linked threat cluster, based on tactics, techniques, and procedures observed in the campaign.
The backend command-and-control infrastructure at bsnowcommunications[.]com remained active even after user-facing domains were taken offline, indicating compartmentalized operations designed to maintain access to already-compromised systems while protecting core infrastructure from discovery.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.



