A major gang that sells a secret data-stealing tool called Lumma Stealer, a highly adaptable Malware-as-a-Service (MaaS) marketed since 2022 to steal everything from passwords and credit card numbers to crypto wallets, is now in deep trouble.
According to a recent report by the research firm Trend Micro, which tracked the group as Water Kurita, rival criminals launched a campaign to expose its members. This internal fight among cybercriminals has caused a huge, sudden drop in Lumma Stealer’s observed activity since September 2025.
Identities Exposed
The trouble started between late August and early October 2025 when a “doxxing” campaign began publishing sensitive personal and operational details of five people, allegedly the masterminds of the Lumma Stealer operation.
The exposed details, which were shared on a website called “Lumma Rats,” reportedly included sensitive data like passport numbers, financial records, and emails of those involved in both the administrative and technical sides, such as those responsible for ‘crypter development,’ which means hiding the malware code to avoid detection.
Trend Micro’s research revealed that this was likely driven by competitors, especially after a coordinated law enforcement attempt to shut down Lumma Stealer in May 2025 failed to stop it completely.
This disruption, which was reported by Hackread.com, followed reports of Lumma’s global infection patterns in North America, Europe, and Asia, and involved Microsoft and global partners seizing over 2,300 domains.
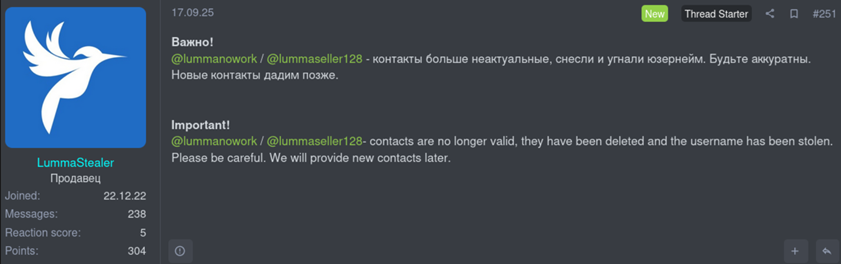
The intensity of the recent leaks suggests either insider knowledge or access to compromised accounts. The situation worsened on September 17, 2025, when the group’s official Telegram accounts were also compromised, severely hurting their ability to talk to their clients.
Customers Shift to New Options
As Lumma Stealer’s command-and-control (C2) infrastructure (the network that tells the malware what to do) began to fail, its customers started looking for new places to get their malware.
This sudden instability has triggered aggressive competition, as other malware developers try to capture the market. The primary replacement choices gaining popularity are MaaS platforms called Vidar and StealC.
In fact, other related services, like the pay-per-install (PPI) service Amadey, which criminals use to deliver infostealer malware to victims’ computers, have also seen reduced demand. This shows just how much this internal fight has shaken up the entire cybercrime community, proving that even the most dominant players can fall victim to the very unpredictable nature of the underground market.