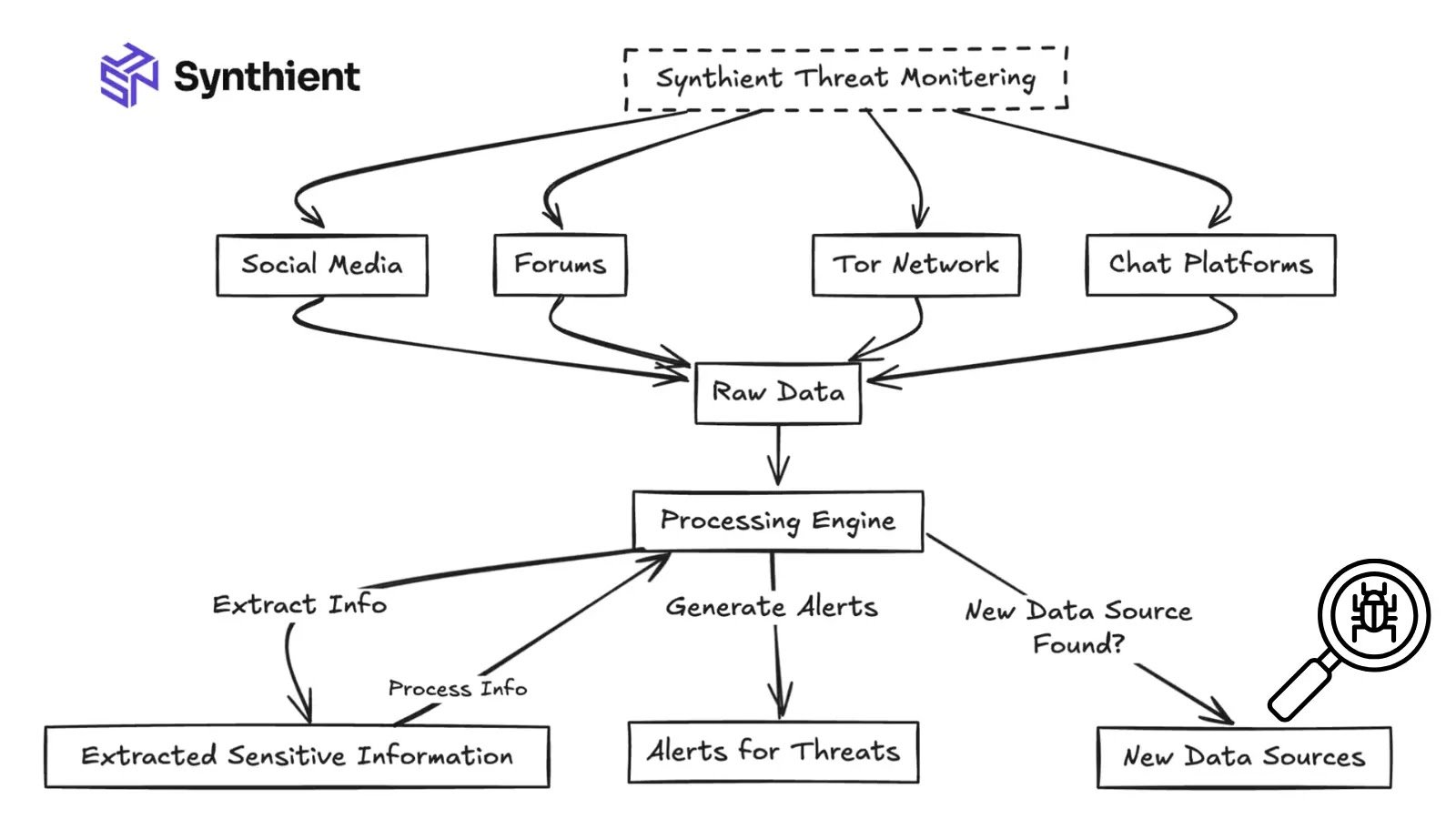
The cybercrime ecosystem surrounding stealer malware has reached unprecedented scale, with threat actors now processing millions of stolen credentials daily through sophisticated distribution networks.
Security researchers have been monitoring these operations for nearly a year, revealing an alarming infrastructure that processes victim data at industrial volumes through platforms like Telegram, forums, and social media sites.
The stealer log ecosystem has undergone significant transformation over recent years, evolving from scattered operations into highly organized criminal enterprises.
Researchers who began monitoring these platforms implemented a comprehensive data ingestion system designed to help victims, partnering with Have I Been Pwned to alert individuals whose credentials had been compromised.
The monitoring infrastructure was built to rival the largest threat intelligence platforms, focusing on capturing unique data and achieving near real-time alerting capabilities.
The research revealed that Telegram emerged as the primary data driver within the stealer ecosystem, capable of contributing millions of unique credentials within a single day.


At peak activity, a single Telegram account could process as many as 50 million credentials in 24 hours. This staggering volume highlights the industrial scale at which credential theft operations now function, far exceeding previous estimates of cybercrime capabilities.
Criminal Marketplace Structure
The stealer log ecosystem operates through a hierarchical structure with distinct roles and responsibilities.
Primary sellers manage key operations, typically maintaining both public channels where samples are shared and paid private channels where clients purchase access to fresh stealer logs.
These operators coordinate with traffers who distribute malware through various infection vectors, while aggregators collect and redistribute logs across multiple channels.


Aggregators play a particularly interesting role in this ecosystem, often leaking data publicly to gain attention and build reputation within criminal communities.
They merge files from multiple sources, creating unique compilations that complicate tracking efforts.
Primary sellers frequently password-protect their archives with links to their channels to prevent aggregators from claiming credit, adding additional layers of complexity to the data distribution process.
Researchers developed a sophisticated monitoring infrastructure using Telegram’s MTProto wire format, deploying approximately 20 premium Telegram accounts as workers dedicated to monitoring and scraping channels.


These workers operated message listeners that forwarded incoming messages to processors, which then extracted invite links, identified attachments, and forwarded files to a decoupled downloading engine for extraction and processing.
The system incorporated multiple deduplication mechanisms to handle the massive volume of redundant data.
Files were checked using Telegram’s FileHash before downloading, with a second deduplication layer implemented through ClickHouse using ReplacingMergeTree architecture.
This approach allowed researchers to track how widely certain credentials were distributed across the criminal ecosystem while managing storage constraints.


The processor inspected messages for stolen data indicators, instructing workers to join relevant channels automatically.
Downloaded files were analyzed to determine their format before parsing, with data batch-inserted into ClickHouse databases for analysis. Successfully processed files were deleted immediately to conserve storage space, given the enormous daily volumes being processed.
Identifying Malicious Infrastructure
The research team focused specifically on adversary infrastructure by starting with known malicious Telegram channels and using them as seed data.
Channels referenced by multiple malicious sources received higher malicious probability rankings and were prioritized for crawling.
This approach allowed researchers to map the interconnected network of credential theft operations while avoiding false positives from legitimate channels.
The diversity of data formats posed significant challenges, as different malware families and traffers used varying output structures.
Primary sellers, aggregators, and traffers each employed unique formatting conventions, with no consistency across the ecosystem. This required flexible parsing capabilities to extract credentials from the wide range of file formats encountered.
The research team ultimately donated their collected data to Have I Been Pwned rather than monetizing it, citing concerns about platforms that allow anyone with a credit card to access victim details without proper verification.
By providing the dataset to Have I Been Pwned, researchers aimed to help victims secure their accounts without suffering further exploitation from threat intelligence platforms that lack adequate safeguards against misuse of stolen credential data.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.