Security researchers are tracking a high-severity malware campaign that uses weaponized PDF files to distribute the Winos 4.0 malware.
The threat actors impersonate government departments to trick users into opening malicious documents that infect Microsoft Windows machines.
The campaign, first observed in early 2025, has since expanded its operations from Taiwan to Japan and Malaysia, evolving its tactics to evade detection.


Phishing Lures and Geographic Expansion
The attack begins with a phishing email containing a PDF that appears to be an official document from a government agency, such as the Ministry of Finance.
These PDFs are embedded with malicious links that, when clicked, initiate the malware download. Initially, the threat actors used Tencent Cloud storage to host the payloads, but they later shifted to custom domains.
Researchers from FortiGuard Labs were able to connect various attacks by analyzing unique IDs in the cloud storage URLs, which revealed that the same threat actor was behind campaigns in different regions.


For example, one PDF targeting users in Taiwan redirected victims to a Japanese-language page to download a malware payload, linking the attacks across both countries.
- PDFs mimic government documents to gain credibility and lure victims into compliance.
- Malicious links are often disguised as embedded resources, making detection harder for recipients.
- Researchers traced links and IDs to uncover the infrastructure behind these campaigns.
- Attackers repurpose infrastructure and tactics to adapt to different regions and languages.
Sophisticated Evasion Techniques
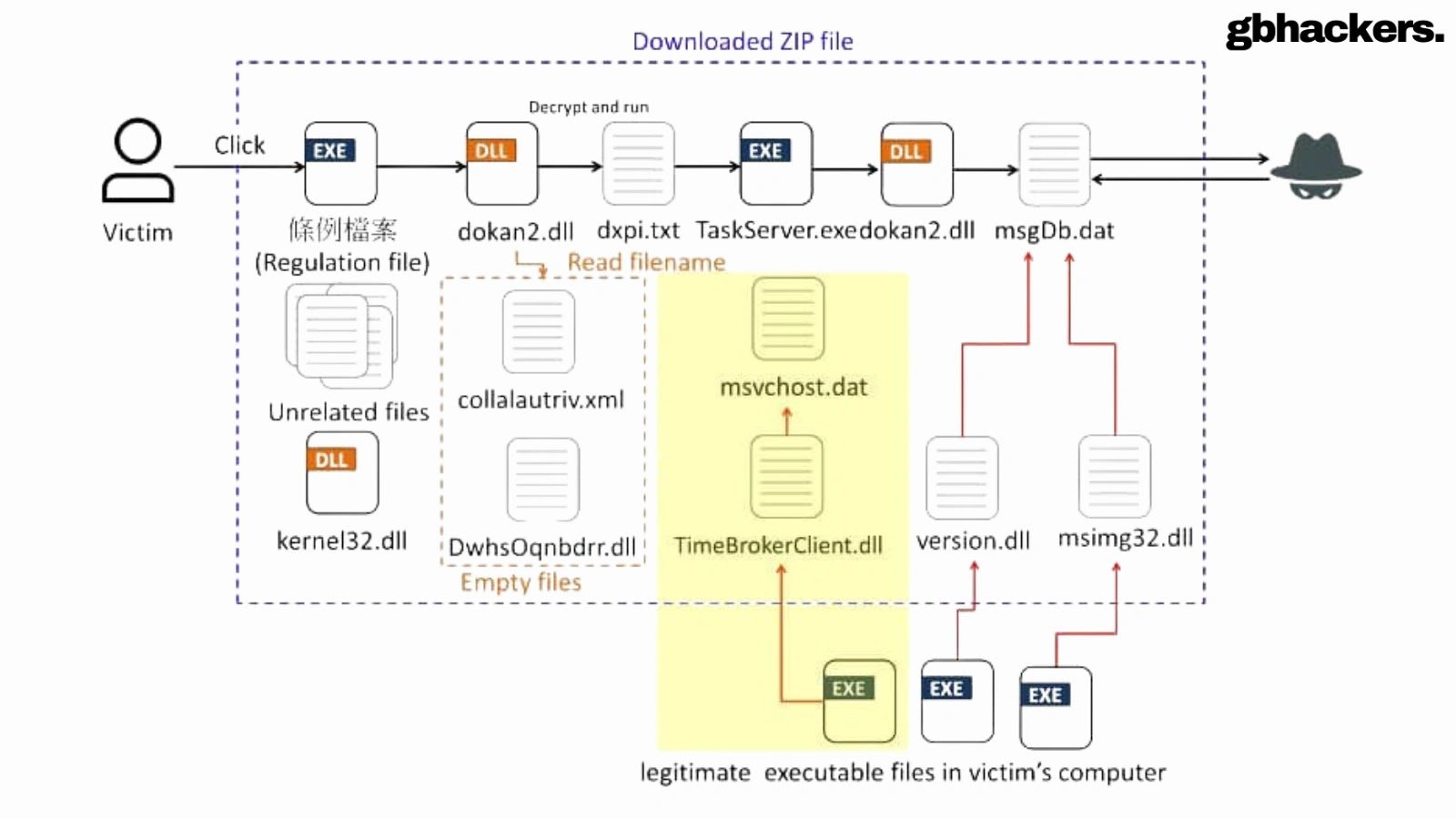
The threat actors have continuously refined their methods to avoid security software and analysis. In recent attacks, the campaign has switched from Winos 4.0 to a newer malware family called HoldingHands.


This malware is delivered through a complex, multi-stage infection process that uses legitimate-looking executables and DLL side-loading to bypass defenses. One of the most significant changes in the malware’s latest variant is its use of the Windows Task Scheduler to execute its components.
By terminating and then allowing the Task Scheduler service to restart, the malware can launch its processes indirectly, making its behavior much harder to detect through traditional monitoring. This stealthy trigger mechanism allows the payload to run with elevated privileges while leaving fewer forensic artifacts.
- HoldingHands replaces Winos 4.0 as the main payload, adding infrastructure shifting via registry updates.
- Multi-stage execution flow involves DLL side-loading and indirect process triggering.
- The use of Windows Task Scheduler seriously complicates behavior-based detection, as tasks can be hidden and automatically restarted.
- Malware conducts antivirus product checks and only executes if protections are absent, increasing infection success.
A Persistent and Evolving Threat
The HoldingHands payload itself is designed for information theft, which can be used to facilitate future attacks. It has the ability to check for the presence of antivirus products like Norton, Avast, and Kaspersky and will terminate itself if certain security processes are found.
By connecting shared infrastructure, code patterns, and operational tactics, researchers have been able to link seemingly isolated incidents into a single, coordinated campaign spanning multiple countries.
The group’s ability to evolve its malware and delivery mechanisms highlights a persistent and adaptable threat to organizations across Asia. The stolen information poses a significant risk, as it can be leveraged for more targeted and damaging cyberattacks.
Indicators of Compromise (IoCs):
| Domain | IP | SHA256 |
|---|---|---|
| zxp0010w.vip | 206.238.199.22 | c138ff7d0b46a657c3a327f4eb266866957b4117c0507507ba81aaeb42cdefa9 |
| gjqygs.cn | 206.238.221.244 | 03e1cdca2a9e08efa8448e20b50dc63fdbea0e850de25c3a8e04b03e743b983d |
| zcqiyess.vip | 206.238.199.22 | 2b1719108ec52e5dea20169a225b7d383ad450195a5e6274315c79874f448caa |
| jpjpz1.cc | 154.91.64.45 | dc45981ff705b641434ff959de5f8d4c12341eaeda42d278bd4e46628df94ac5 |
| jppjp.vip | 156.251.17.12 | 0db506d018413268e441a34e6e134c9f5a33ceea338fc323d231de966401bb2c |
| jpjpz1.top | 206.238.221.182 | 031c916b599e17d8cfa13089bddafc2436be8522f0c9e479c7d76ba3010bbd18 |
| (none) | 38.60.203.110 | c6095912671a201dad86d101e4fe619319cc22b10b4e8d74c3cd655b2175364c |
| (none) | (none) | 03e1cdca2a9e08efa8448e20b50dc63fdbea0e850de25c3a8e04b03e743b983d |
| (none) | (none) | 2b1719108ec52e5dea20169a225b7d383ad450195a5e6274315c79874f448caa |
| (none) | (none) | dc45981ff705b641434ff959de5f8d4c12341eaeda42d278bd4e46628df94ac5 |
| (none) | (none) | 804dc39c1f928964a5c02d129da72c836accf19b8f6d8dc69fc853ce5f65b4f3 |
| (none) | (none) | 1c4bc67ae4af505f58bd11399d45e196fc17cc5dd32ad1d8e6836832d59df6e6 |
| (none) | (none) | fb9c9ed91fc70f862876bd77314d3b2275069ca7c4db045e5972e726a3e8e04c |
| (none) | (none) | 8d25da6459c427ad658ff400e1184084db1789a7abff9b70ca85cf57f4320283 |
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.