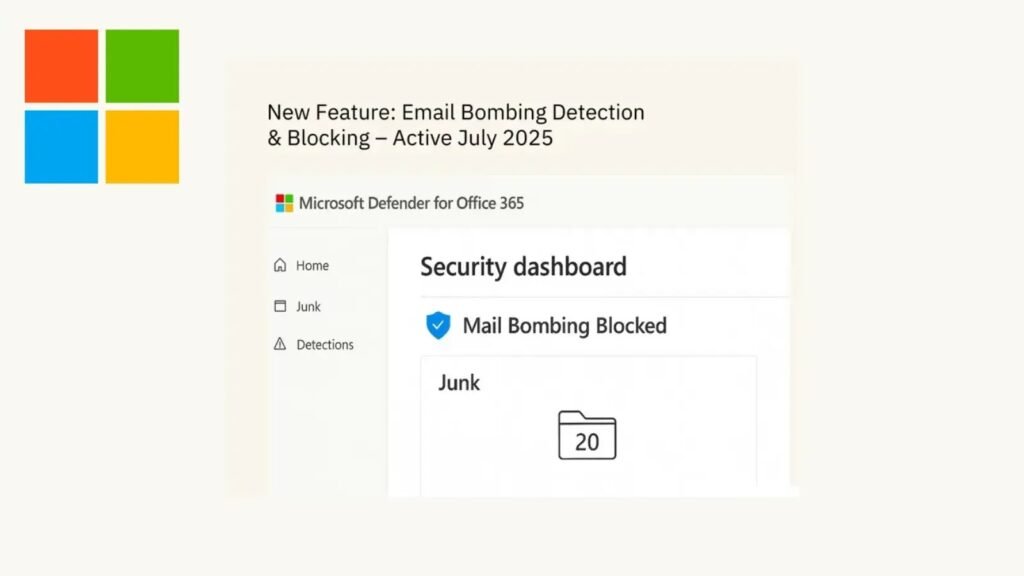
Microsoft has announced a significant security upgrade for its Office 365 platform, introducing a new Mail Bombing Detection feature within Microsoft Defender for Office 365.
This enhancement, rolling out globally from late June through early July 2025, is designed to automatically identify and block email bombing attacks—a growing threat that floods user inboxes with massive volumes of messages to obscure critical communications or overwhelm systems.
Understanding Email Bombing and Its Risks
Email bombing, also known as spam bombing, is a cyberattack technique where attackers send thousands—or even tens of thousands—of emails to a target mailbox in a short period.
The intent is not only to disrupt operations but also to hide important security alerts or facilitate follow-up attacks such as phishing, ransomware, or data theft.
Recent trends show attackers coupling email bombing with social engineering: after the victim’s inbox is flooded, attackers may impersonate IT support via phone or video call, leveraging the chaos to trick users into installing malware or divulging sensitive information.
The new Mail Bombing Detection capability leverages advanced machine learning and AI-driven analytics to monitor message volumes, sender patterns, and spam signals across different sources and time intervals.
When a mail bombing campaign is detected, affected messages are automatically routed to the Junk folder, sparing users from inbox overload while ensuring legitimate communications from Safe Senders remain unaffected.
This feature is enabled by default and requires no manual configuration, streamlining protection for organizations of all sizes.
Key highlights include:
- Automatic detection and blocking: Suspicious campaigns are identified and neutralized without admin intervention.
- Seamless integration: The feature works within existing Defender for Office 365 environments.
- Visibility for security teams: Security Operations Center (SOC) analysts and administrators can track mail bombing incidents via new detection types in Threat Explorer, Email entity views, and Advanced Hunting tools.
- No disruption to Safe Senders: Messages from trusted sources are not misclassified, reducing the risk of false positives.
Impact and Guidance for Organizations
With this update, organizations gain a robust, automated defense against a disruptive and increasingly common attack vector. Security teams are advised to:
- Inform relevant personnel about the new detection capability.
- Update internal documentation and training materials.
- Review Junk folder handling policies to ensure alignment with organizational needs.
The new detection logic modifies how emails are classified and routed, potentially impacting compliance dashboards, audit logging, or eDiscovery visibility for messages sent to Junk.
Organizations should review their compliance monitoring practices to accommodate these changes.
By the end of July 2025, all Microsoft Defender for Office 365 customers will have this protection enabled by default, marking a proactive step in safeguarding users from sophisticated email-based threats.
Exclusive Webinar Alert: Harnessing Intel® Processor Innovations for Advanced API Security – Register for Free